Tame the Complexity of Open Source







One platform. Total control.
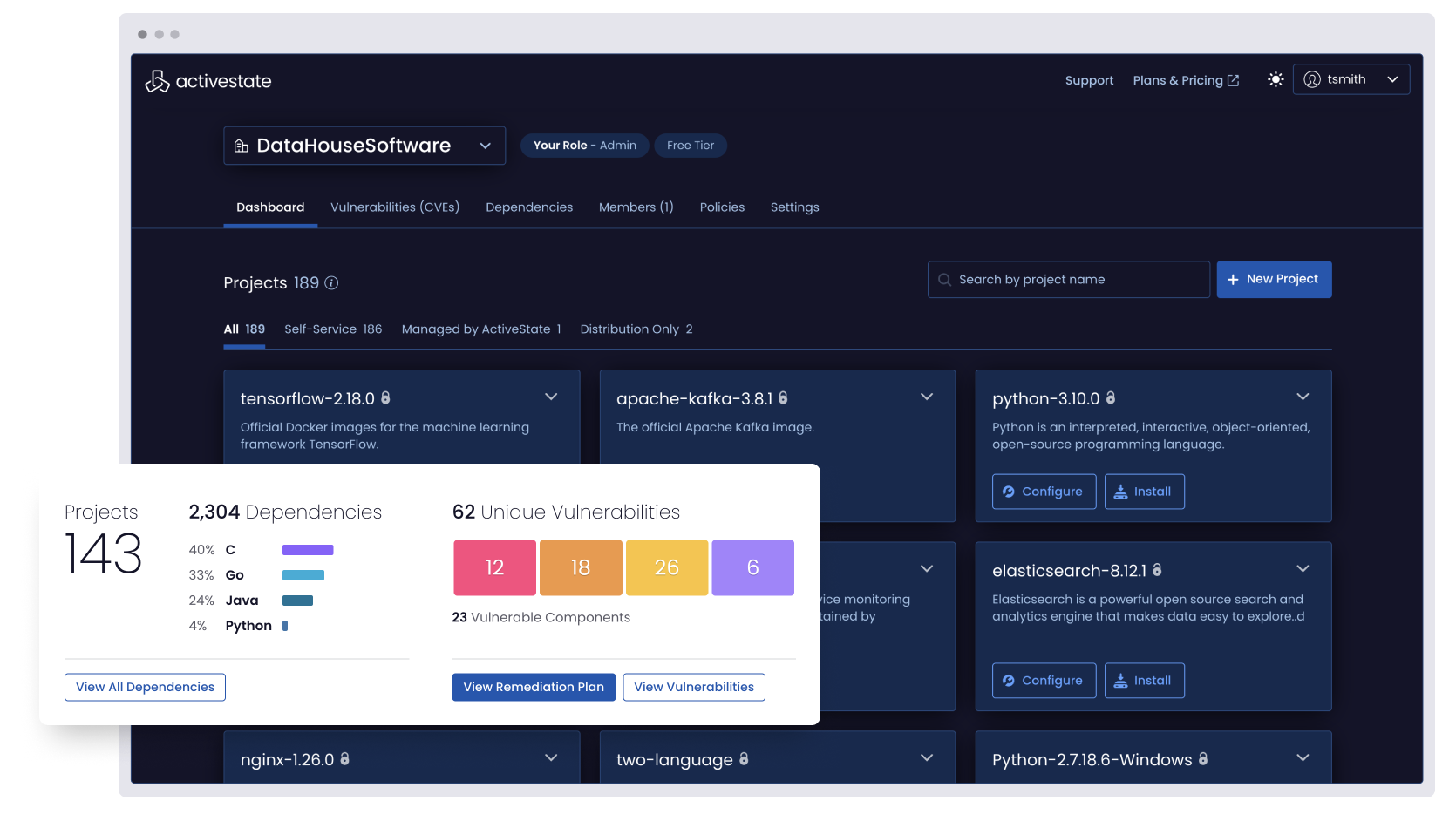
Discover: Unveil your open source landscape
Discover your complete open source landscape with comprehensive ingestion and real-time monitoring across SBOMs, repositories, and Kubernetes clusters.
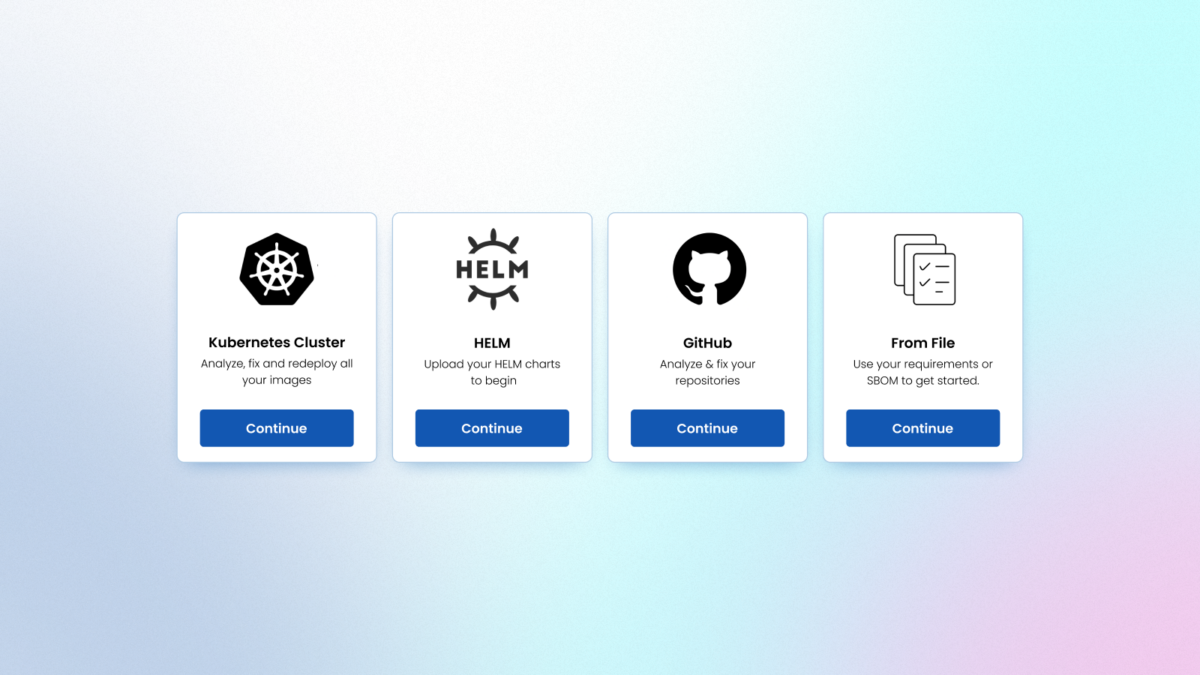
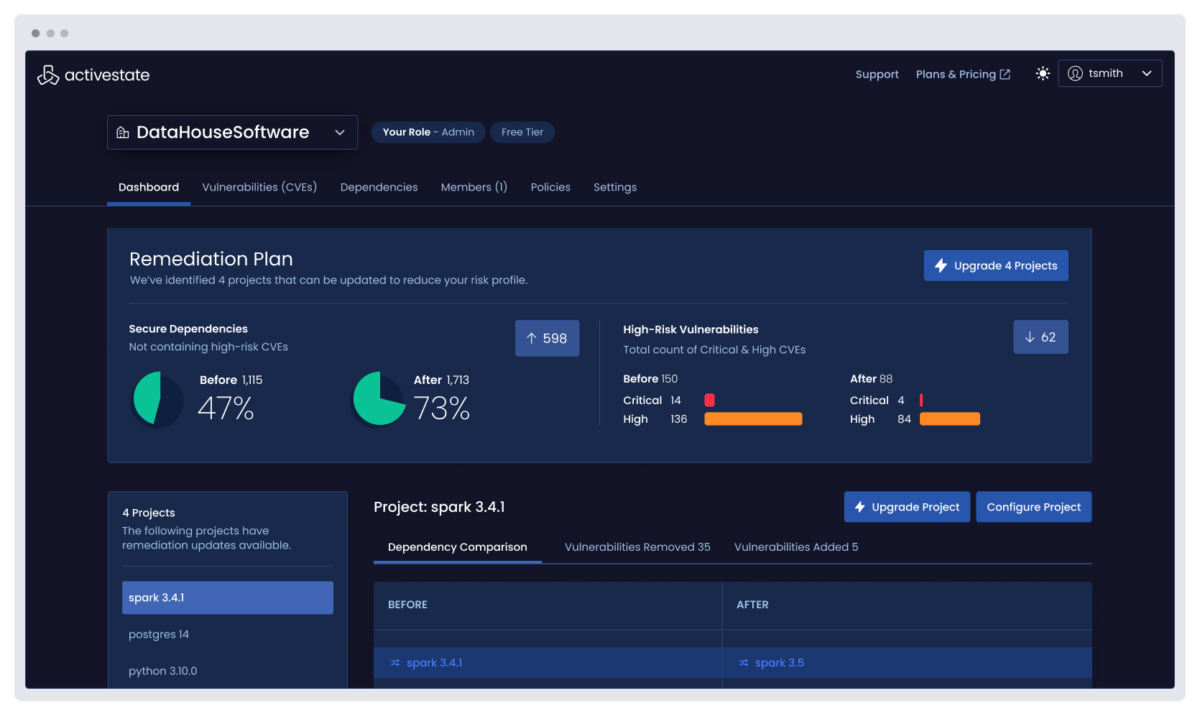
Prioritize: Uncover insights, mitigate risks
Prioritize actions through deep analytics, vulnerability assessments, and upgrade impact analysis that illuminate your risk profile.
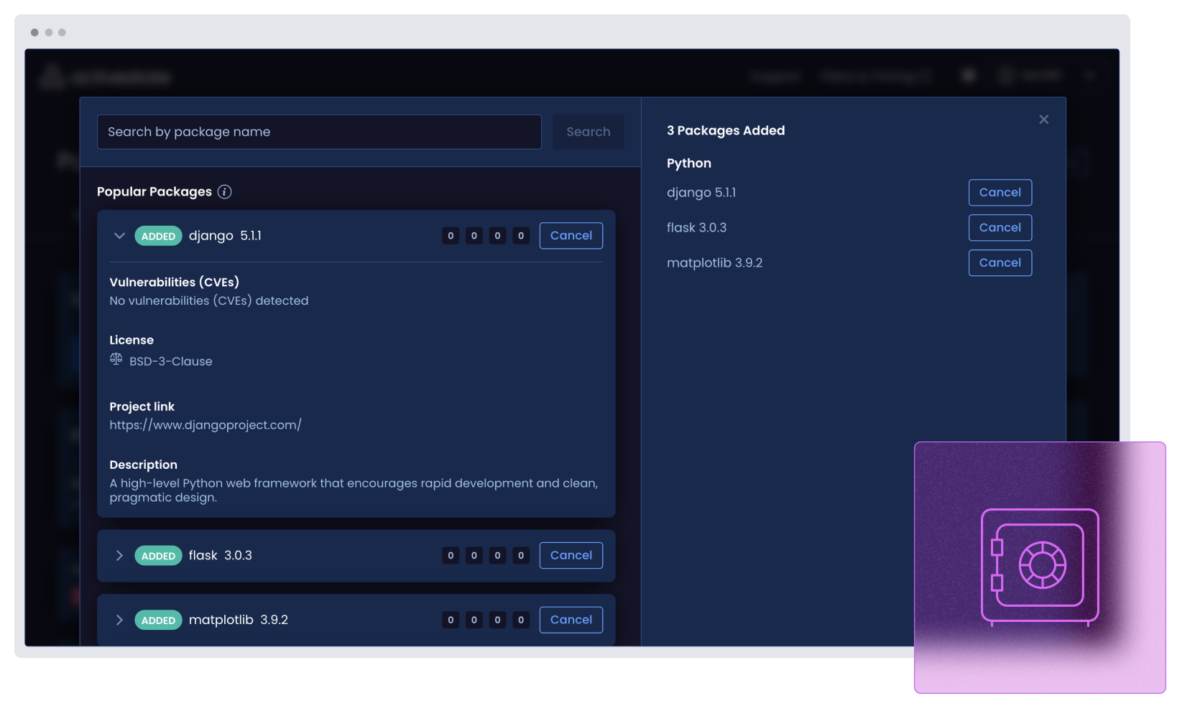
Curate and upgrade: Your secure open source gateway
Curate a secure gateway for trusted components with policy-driven filters and an immutable catalog built from verified source code.
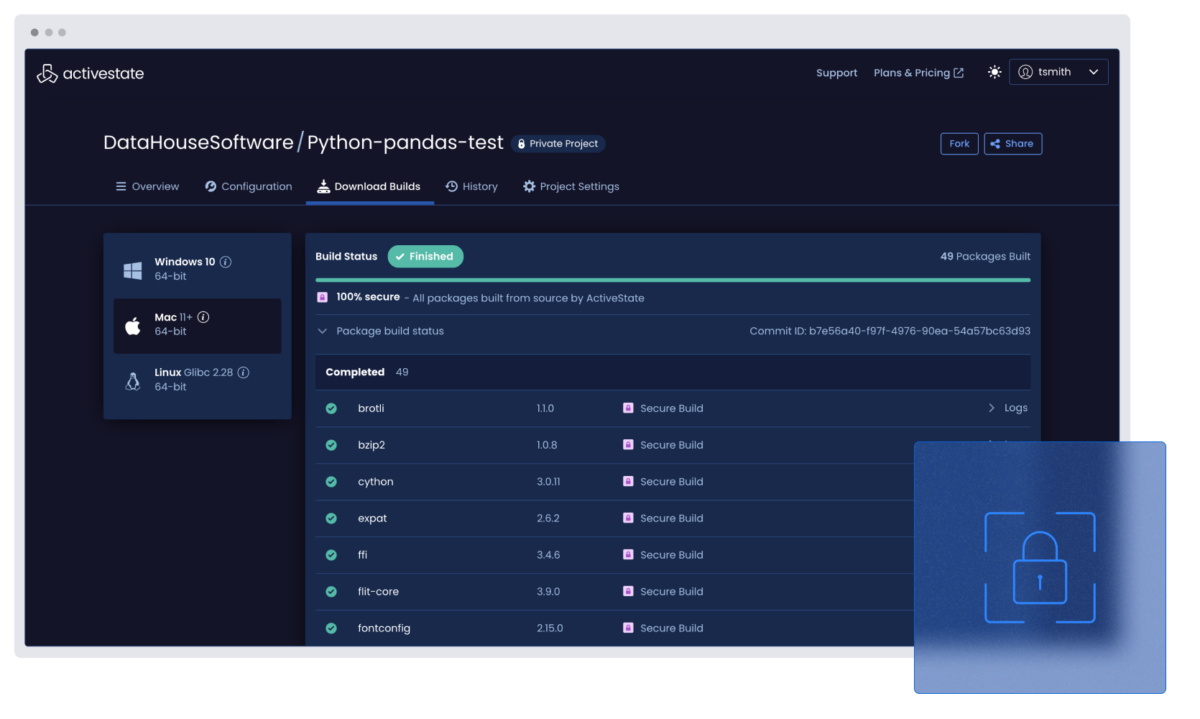
Build and deploy: Your hardened build infrastructure
Build with confidence using our hardened infrastructure that integrates seamlessly into your CI/CD pipeline while maintaining security and compliance.




Additional Resources

ActiveState Empowers Data Scientists with R Language Support, Strengthening Leadership in Open Source Security Posture Management
Company extends its secure, curated open source catalog to secure the data science software supply chain through Intelligent Remediation Vancouver, BC – [24 April 2025]

ActiveState Hits Critical Coverage Milestone for Java Support, Reinforcing Leadership in Intelligent Remediation for Vulnerability Management
With comprehensive Java coverage at 13M+ in its curated OSS catalog driven by on-demand catalog expansion, ActiveState further expands its industry-leading catalog of secure open

AI-Powered Vulnerability Management: The Key to Proactive Enterprise Threat Detection
AI is no longer a novelty. Nearly all of the tools modern enterprise software teams rely on, from project management and code intelligence to security



