Tame the Complexity of Open Source







One platform. Total control.
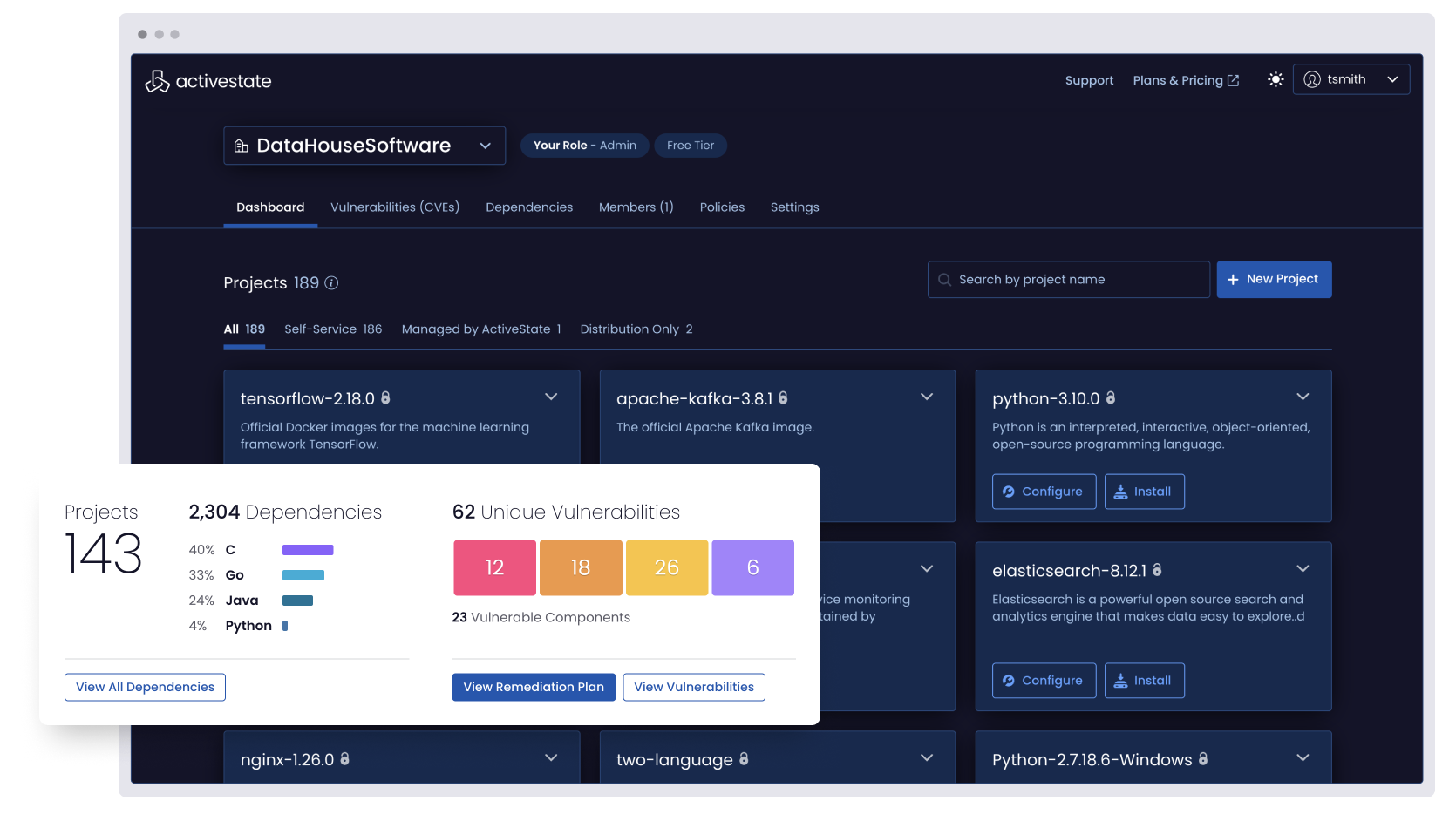
Discover: Unveil your open source landscape
Discover your complete open source landscape with comprehensive ingestion and real-time monitoring across SBOMs, repositories, and Kubernetes clusters.
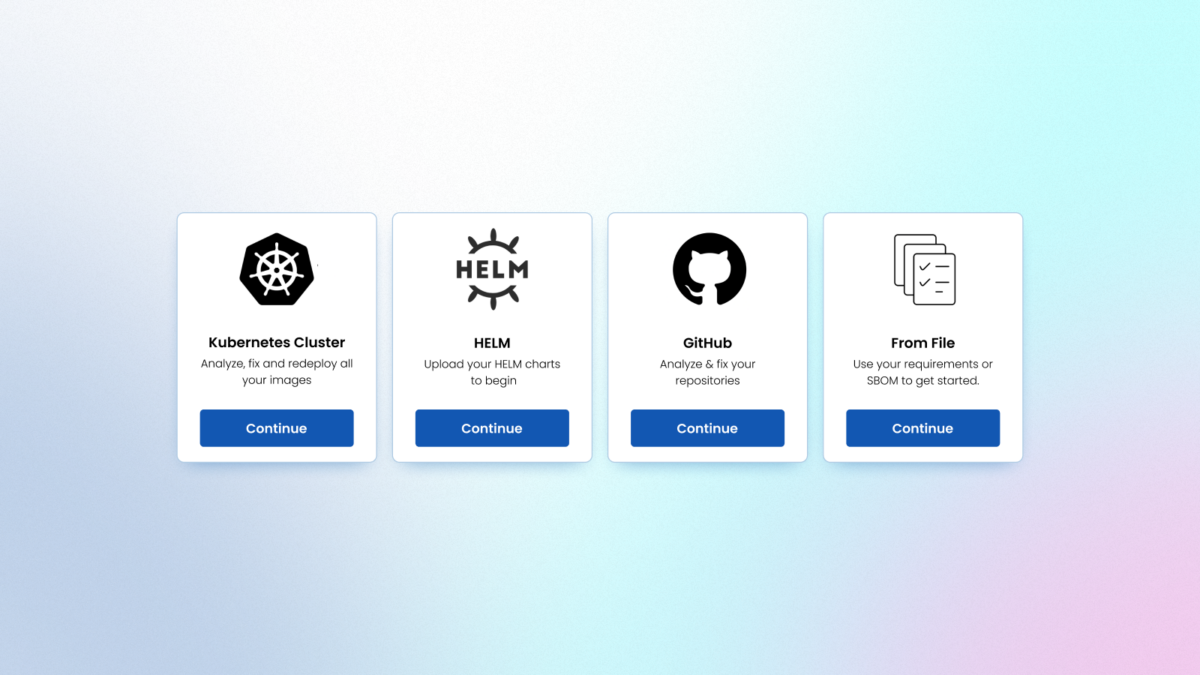
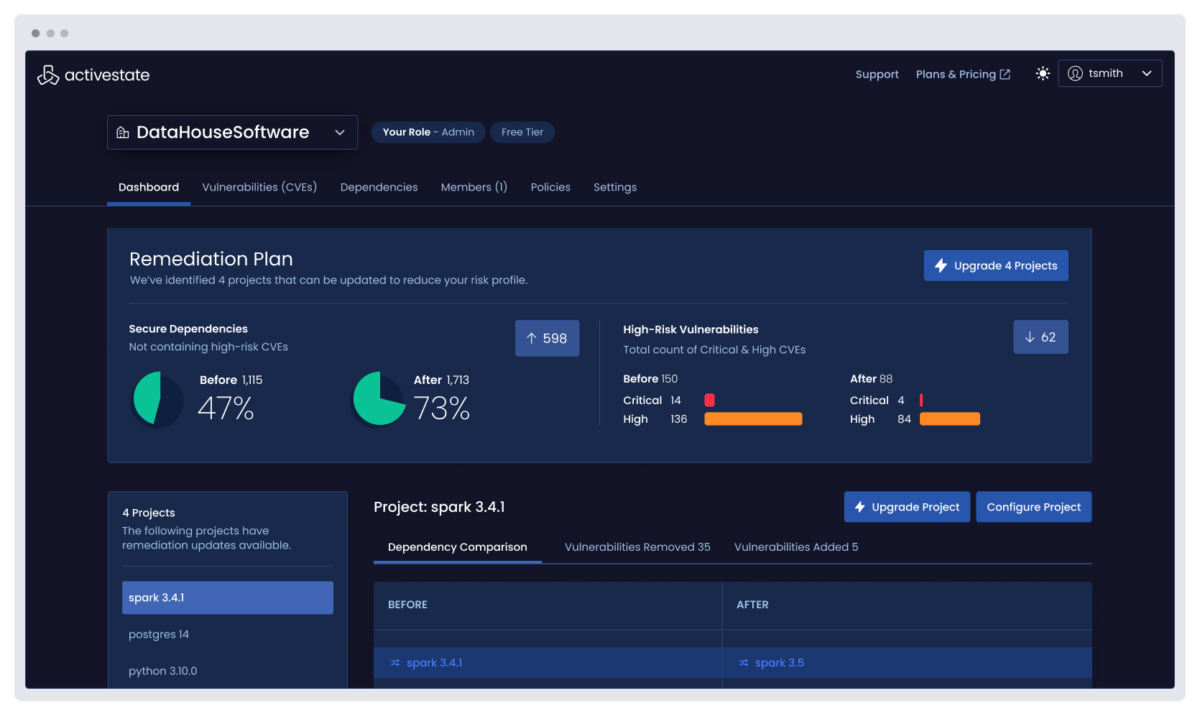
Prioritize: Uncover insights, mitigate risks
Prioritize actions through deep analytics, vulnerability assessments, and upgrade impact analysis that illuminate your risk profile.
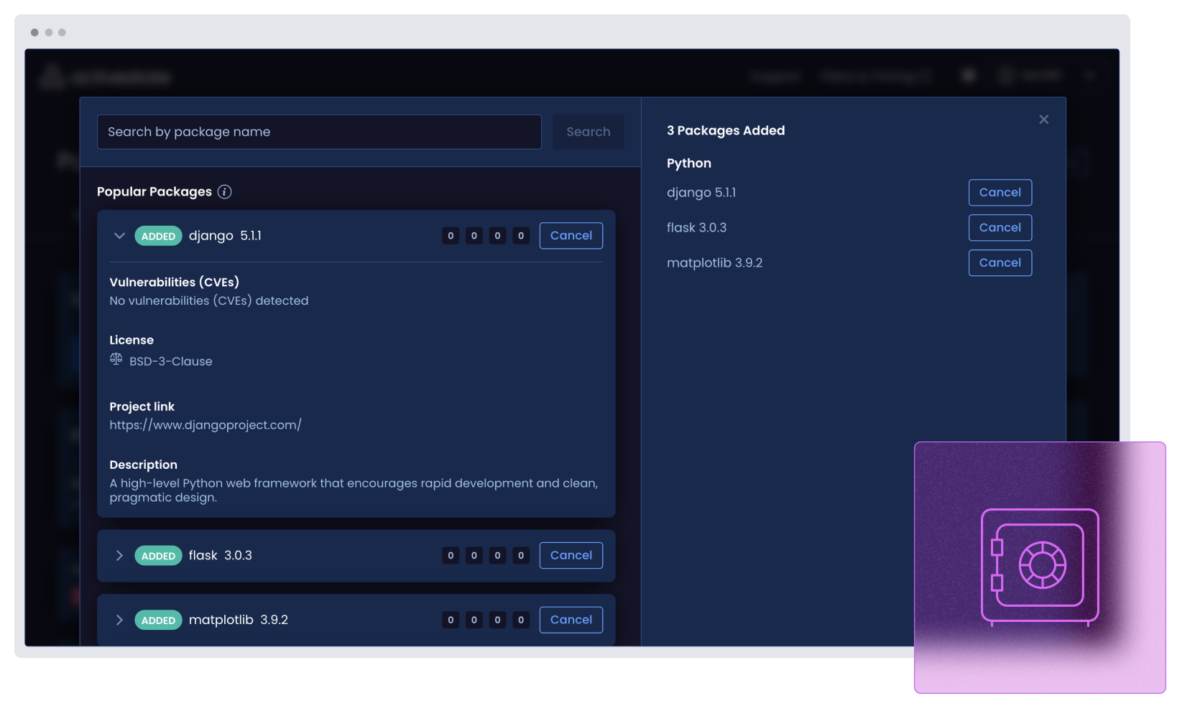
Curate and upgrade: Your secure open source gateway
Curate a secure gateway for trusted components with policy-driven filters and an immutable catalog built from verified source code.
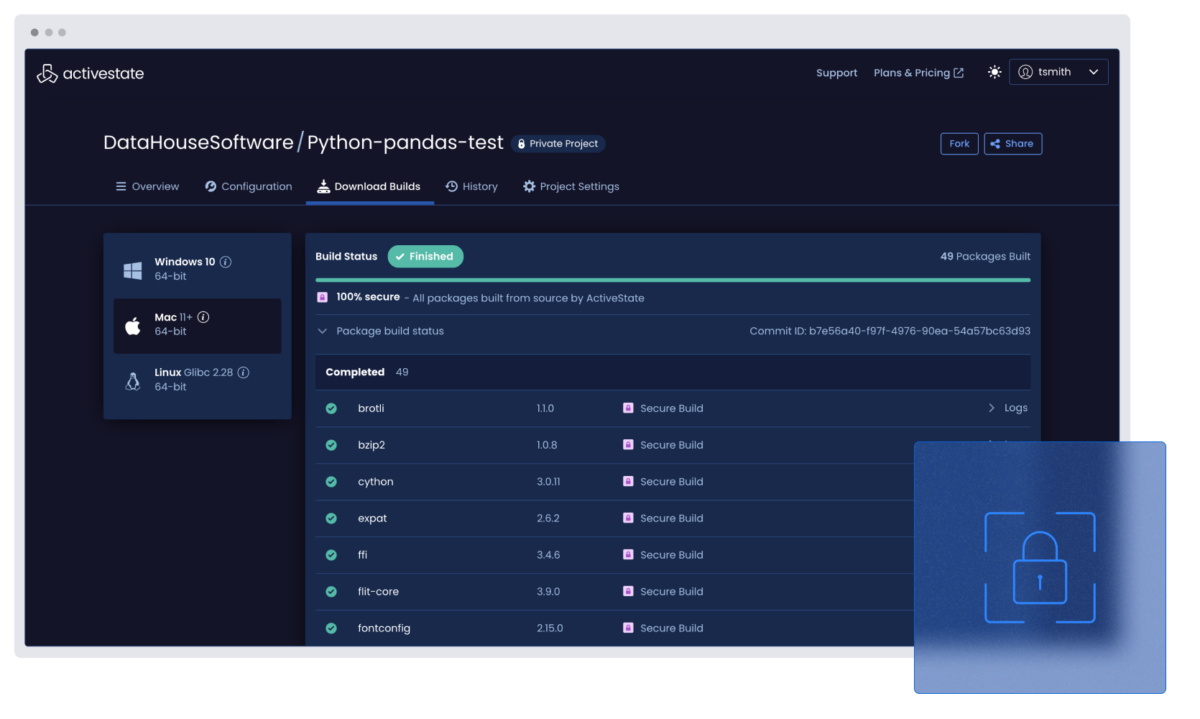
Build and deploy: Your hardened build infrastructure
Build with confidence using our hardened infrastructure that integrates seamlessly into your CI/CD pipeline while maintaining security and compliance.




Additional Resources

AI-Powered Vulnerability Management: The Key to Proactive Enterprise Threat Detection
AI is no longer a novelty. Nearly all of the tools modern enterprise software teams rely on, from project management and code intelligence to security

Navigating the Open Source Landscape: How Financial Institutions are Bridging the Vulnerability Management Gap with ActiveState
The financial services sector operates under a unique confluence of stringent regulatory demands, the need to safeguard vast amounts of sensitive data, and the imperative

Level Up Your Security Game: Top 5 DevSecOps Events to Attend in 2025
The world of software development is evolving at breakneck speed, and with it, the importance of integrating security seamlessly into the development lifecycle – DevSecOps.


