Take the 2023 Software Supply Chain Security Survey
This time around we’ve changed a few questions and added one more to focus on emerging threats and new solutions. At the end of the survey, you’ll be given a score that reflects how far along the journey your organization is toward creating a secure software supply chain.
Thanks in advance for your help!
If you want to understand how things have changed since our last survey, read on.
The Problems with Securing the Software Supply Chain
Two years ago, ActiveState took the barometer of where more than 1500 companies of every shape and size around the globe stood when it came to implementing software supply chain security.
Unfortunately, the results were not encouraging.
Of course, back then, the concept of supply chain security was little known. It was primarily exemplified by the Solarwinds hack, which effectively undermined the trust in signed software and kicked off a tidal wave of copycats. The result has been >740% increase in software supply chain attacks over the past three years.
Nowadays, the term “software supply chain security” is more of a buzzword. Thanks to President Biden’s Executive Order 14028, US government supplier requirements, and worldwide pending software supply chain legislation, more and more software vendors have become aware of the need to address weaknesses in their software supply chain.
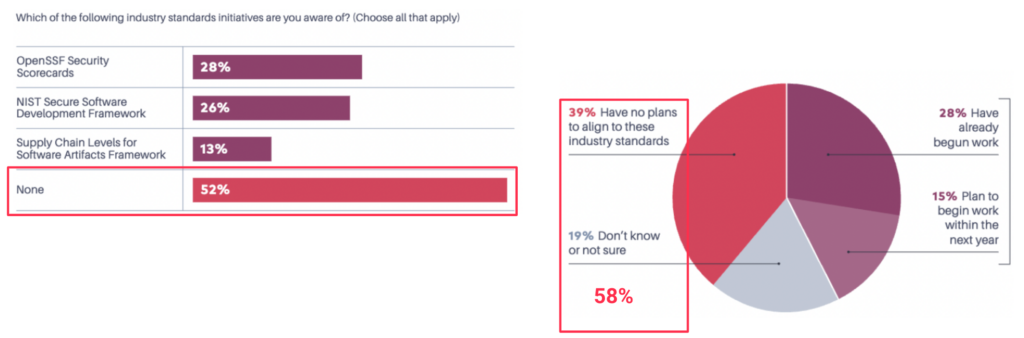
Unfortunately, that awareness has not extended to those that matter the most: open source software maintainers. According to a recent survey by Tidelift, less than half of all maintainers have even heard of (let alone plan to implement) software supply chain security standards:
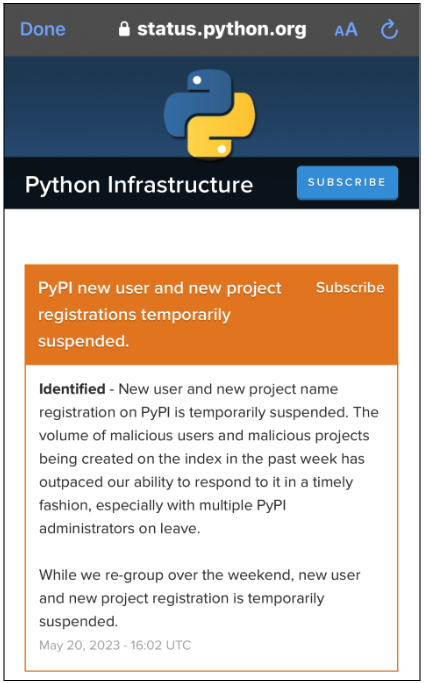
That’s the good guys. The bad guys are continuing to try and take advantage of supply chain weaknesses to the degree that this past week the Python Package Index (PyPI) was forced to suspend the creation of new projects:
And as SAP has highlighted, the vectors of attack used by bad actors just keep expanding:
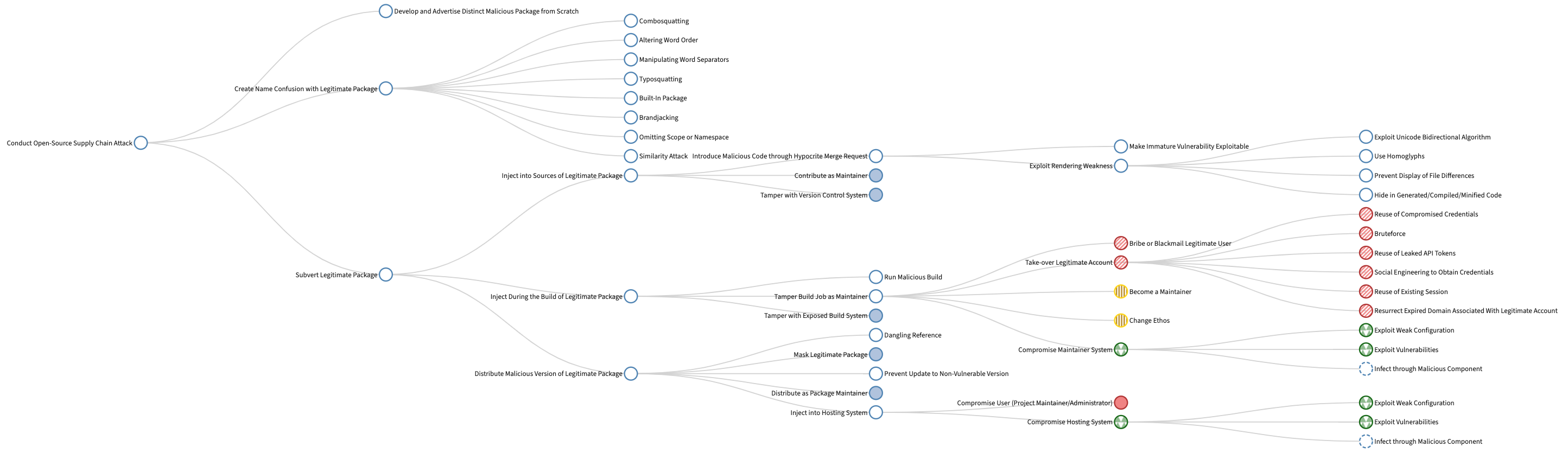
The attack tree shown above organizes attacks and techniques that inject malicious code into open-source software projects, starting from abstract, top-level goals and drilling down to known/ attack techniques.
Software Supply Chain Security in 2023
All of which leads us back to the purpose of this post: to understand where the industry now stands with respect to securing their software supply chain.
The good news is that in 2023, there are a number of market drivers that have recently been gaining strength. For example:
- SLSA – the security framework known as “Secure Levels for Supply chain Artifacts” or SLSA has reached version 1.0, providing organizations with a roadmap to help them implement supply chain security for the software artifacts they import and build.
- SBOMs – Software Bill Of Materials (SBOMs) seem to be everywhere nowadays. Multiple vendors of traditional AppSec software have embraced SBOMs, and now offer it as part of their solution. This is an important step, because these vendors have a large install base of organizations that have adopted traditional Secure Software Development Frameworks (SSDFs), and are now looking to identify and repair weaknesses in their software supply chain.
- Provenance – software attestations are a new concept that can help organizations understand the security and integrity (and thus the risk) of the artifacts they import, such as open source software. While attestation specifications (such as in-toto) are also still very new, a number of vendors are already generating attestations, including:
Given all these initiatives, as well as the continued rise in supply chain attacks – for better or worse – there really is nowhere to hide from software supply chain security these days.
Next steps:
Take our 2-minute/10-question Software Supply Chain Security Survey and find out how your initiatives rank against your peers.
Read Similar Stories

Get the key supply chain security insights for software professionals in 2022 using this 3SC survey report from ActiveState.

The SLSA 1.0 specification provides verifiable controls and best practices to help you secure your software supply chain. Learn how.

Learn how to improve the security & integrity of the open source software components you work with, and how to get ahead of software supply chain risks.






