Secure, vetted open source packages for FinServ teams



Get more with ActiveState
Without ActiveState
With ActiveState
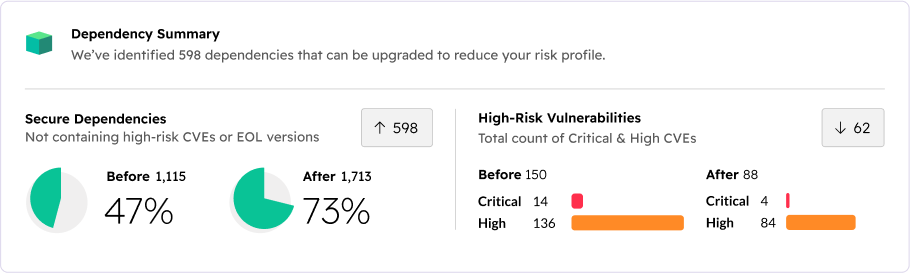
Remediate vulnerabilities
before your customer’s data is breached and exploited.
Manually investigate, patch, rebuild, retest, and redeploy, over and over.
Automatically update and rebuild your runtime, ready for testing, speeding up remediation.
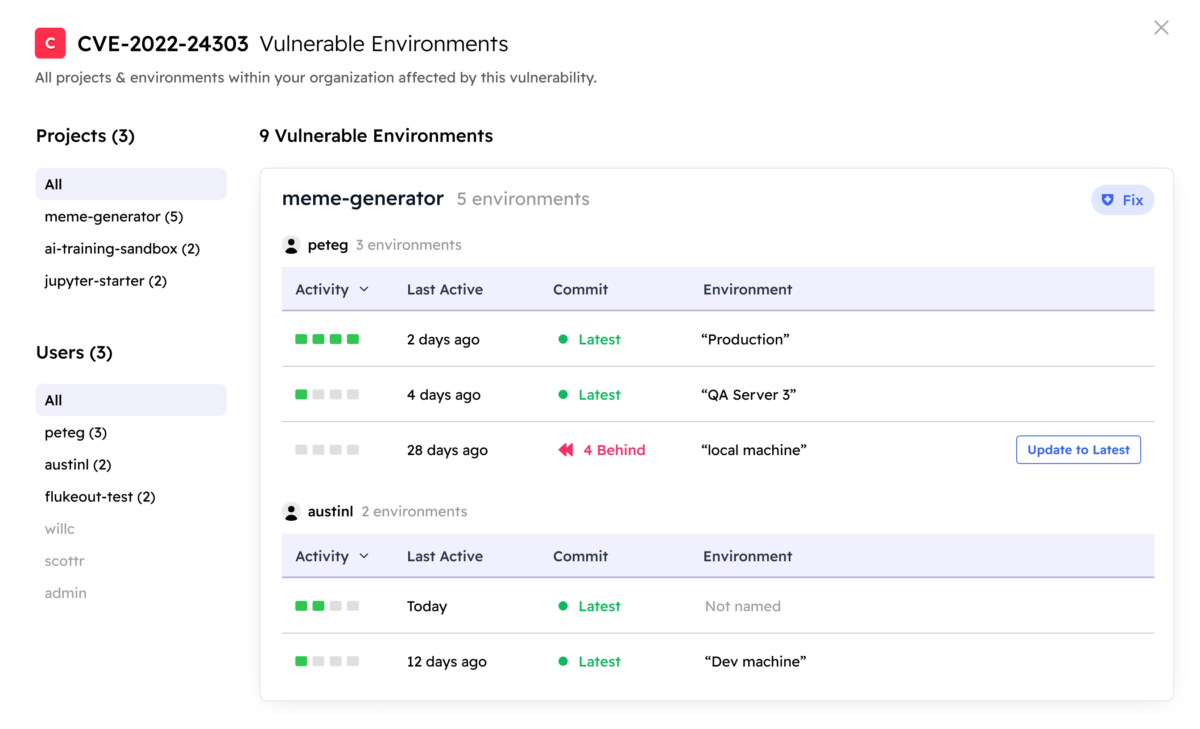
Gain visibility
into all open source software across your enterprise, decreasing time to identification.
An incomplete catalog of open source components generated by scanners and managed in spreadsheets.
A complete online and dynamic catalog of open source components generated from each one’s build tree.
Meet regulations
that continue to get stricter as cyberattacks increase.
More alerts leading to more cybersecurity burnout making it harder to meet SEC disclosure rules.
A secure software supply chain validated by Provenance Attestations and documented by SBOMs.
Read the latest security insights
Rolling out AI apps? Learn the top 5 AI cybersecurity risks they pose, and how to combat them.
Think you have a handle on vendor risk? Learn how to avoid being blindsided by open source vendors.
DevOps
Don’t pause your sprint to fix security issues. Start secure with open source packages built from vetted source code to minimize blowback.
Security
Developers
Don’t pause your sprint to fix security issues. Starting secure with open source packages built from vetted source code minimizes blowback.
Decrease risk and costs by outsourcing the security and maintenance of the open source components from which your software is assembled.
Frequently Asked Questions
What are the top cybersecurity threats facing FinServs?
- Phishing Attacks: the main catalyst in 93% of all data breaches. Source
- Ransomware: 65% of FinServ orgs have been hit paying an average of $2M per incident. Source
- Supply Chain Attacks: More than 75% of software supply chains have experienced cyberattacks in the past 12 months. Source
- Zero-Day Exploits: Zero-day attacks accounted for 14% of successful breaches in the financial sector in 2023. Source
- Insider Threats: 58% of financial services organizations suffered from account takeover attacks, often initiated by insiders. Source
- Advanced Persistent Threats (APTs): APTs were responsible for 23% of attacks against financial institutions in 2023. Source
- Social Engineering: 91% of cyberattacks begin with a spear phishing email, which is a form of social engineering. Source
- Denial-of-Service (DoS) Attacks: The banking and financial services industry vertical claimed the number 1 spot for the highest number of DDoS attacks in 2023 peaking at 35%. Source.
Which open source packages should I be building from source code?
All of them. You can’t count on public repositories when malware-infected packages in 2023 totalled more than twice the total number discovered in the previous 4 years. While public repositories are quick to remove infected packages, usually not before hundreds or even thousands of organizations have been compromised.
ActiveState acts as your private repository for secure packages, building all dependencies in a reproducible manner from vetted source code using a hardened, tamper-proof build system, dramatically reducing the risk of malware.
How can I avoid the “golden dependencies” trap?
- Use a dynamic approach: Maintain a continuously updated catalog of open source components instead of static “blessed” repositories.
- Implement a centralized platform: Use a single source of truth for all stakeholders to foster collaboration and streamline approvals.
- Enhance visibility: Utilize dashboards for clear insights into dependency versions, vulnerabilities, licenses, and deployment locations.
- Enable quick updates: Implement systems for rapid updating of vulnerable components.
Why are binary scanners not enough?
Binary scanners, while useful for detecting known vulnerabilities, are not sufficient on their own for comprehensive security. They primarily identify documented vulnerabilities and may miss new or zero-day threats along with issues introduced in third-party libraries. These tools can generate false positives or negatives, and often lack contextual analysis of how vulnerabilities might be exploited in specific environments. Additionally, binary scanners usually perform static analysis, missing issues that only arise during runtime. Their effectiveness depends on regular updates to their vulnerability databases, and they do not address complex threats like social engineering or advanced persistent threats (APTs).
Why should I trust ActiveState?
Great question! ActiveState has helped enterprises tame open source complexities for more than 25 years. We work with financial organizations like Wells Fargo and Manulife across their Developer, Security, and Operations teams. ActiveState implements the highest SLSA Level 4 controls of any public build platform, ensuring top-tier security for software artifacts.
The ActiveState platform offers automated, tamper-proof builds of open source dependencies from source code, including native libraries, and maintains a perpetual catalog of source code for guaranteed build reproducibility. With enhanced visibility through enriched dependency metadata, FinServ firms gain better control over vulnerabilities and licensing risks. By choosing ActiveState, FinServ organizations can significantly enhance their cybersecurity posture and efficiently manage open source risks with a cost-effective, industry-proven solution, allowing them to focus on their core financial services while ensuring robust security measures are in place.






