Keep Legacy Languages Safe and Secure
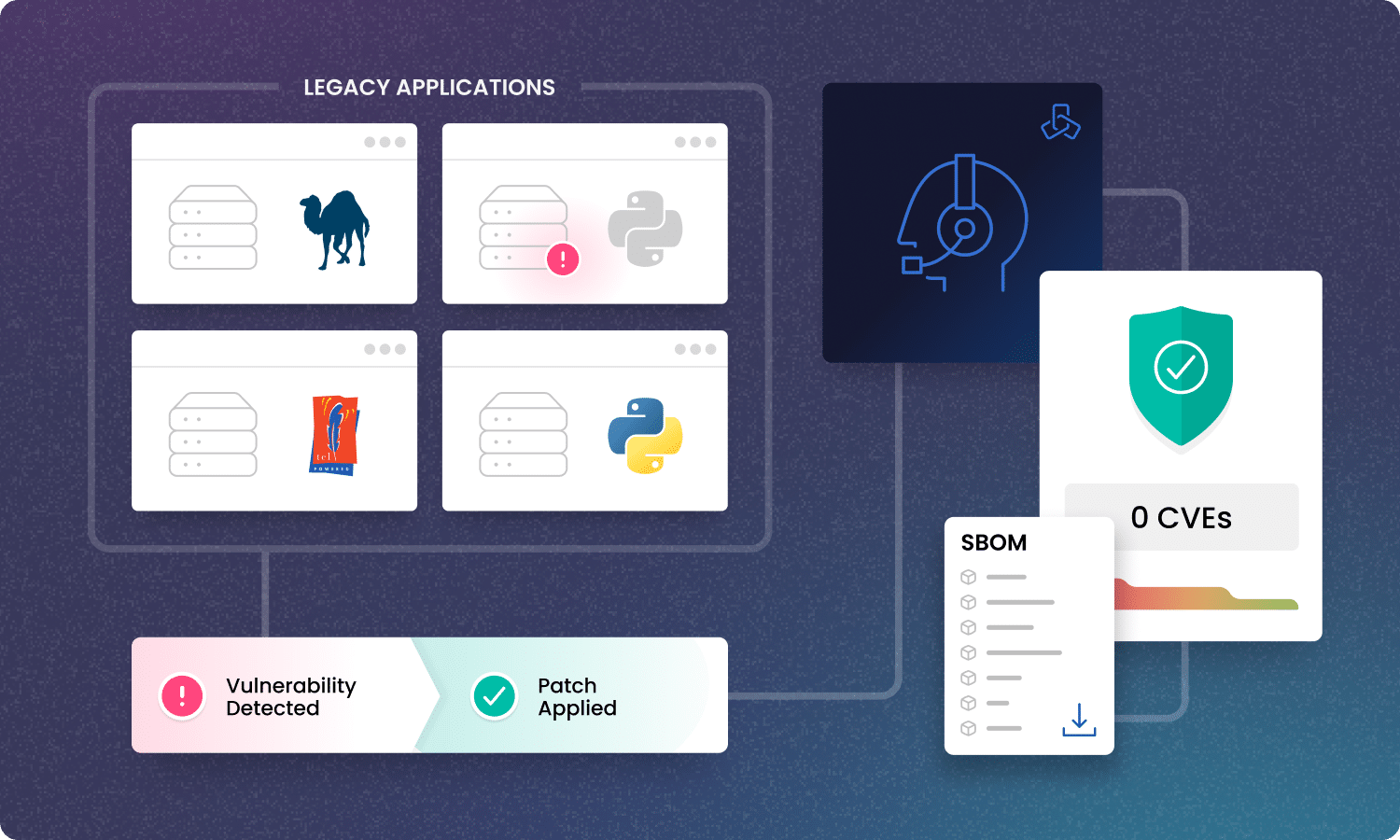







Don’t rewrite. Reinforce.
Stay compliant and secure, without ripping and replacing mission-critical code. ActiveState makes it possible to:
- Build and maintain EOL language versions from source
- Backport security fixes from newer versions
- Ensure software bills of materials (SBOMs) are accurate and auditable
“PCI audits require secure code and builds because of the customer data that the company stores. ActiveState’s Python 2.7 interpreter empowered us to secure Python 2.7 quickly and efficiently.”
– Michael Connolly, Director of Data Services & Engineering

Legacy doesn’t have to mean liability
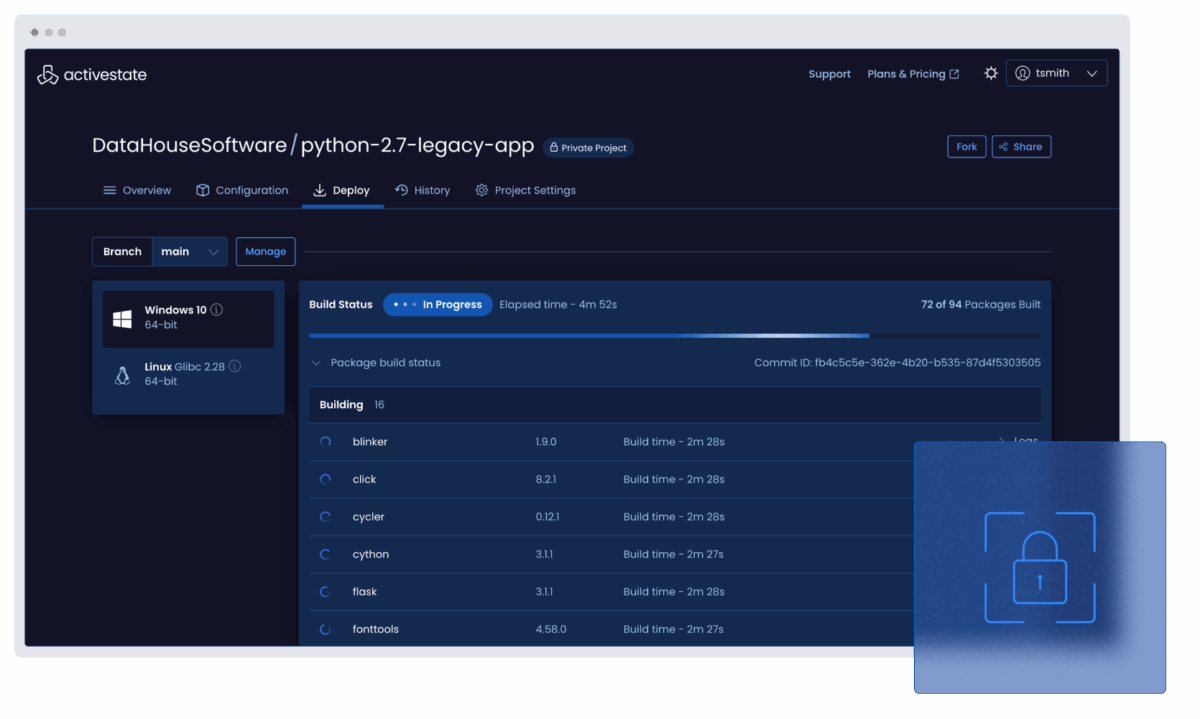
Rebuild outdated languages from source
Automatically build and maintain your EOL language environments using the same secure pipeline we apply to modern versions.
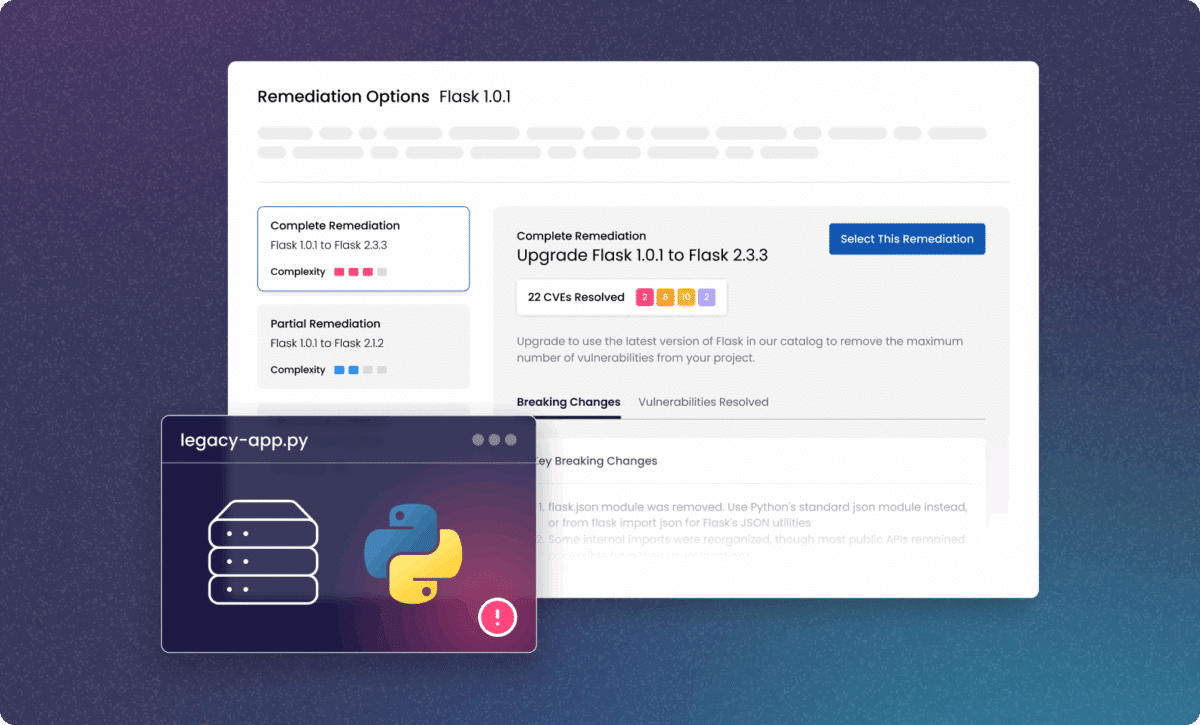
Backport security fixes with confidence
Apply up-to-date security patches from maintained versions without breaking existing dependencies or workflows.
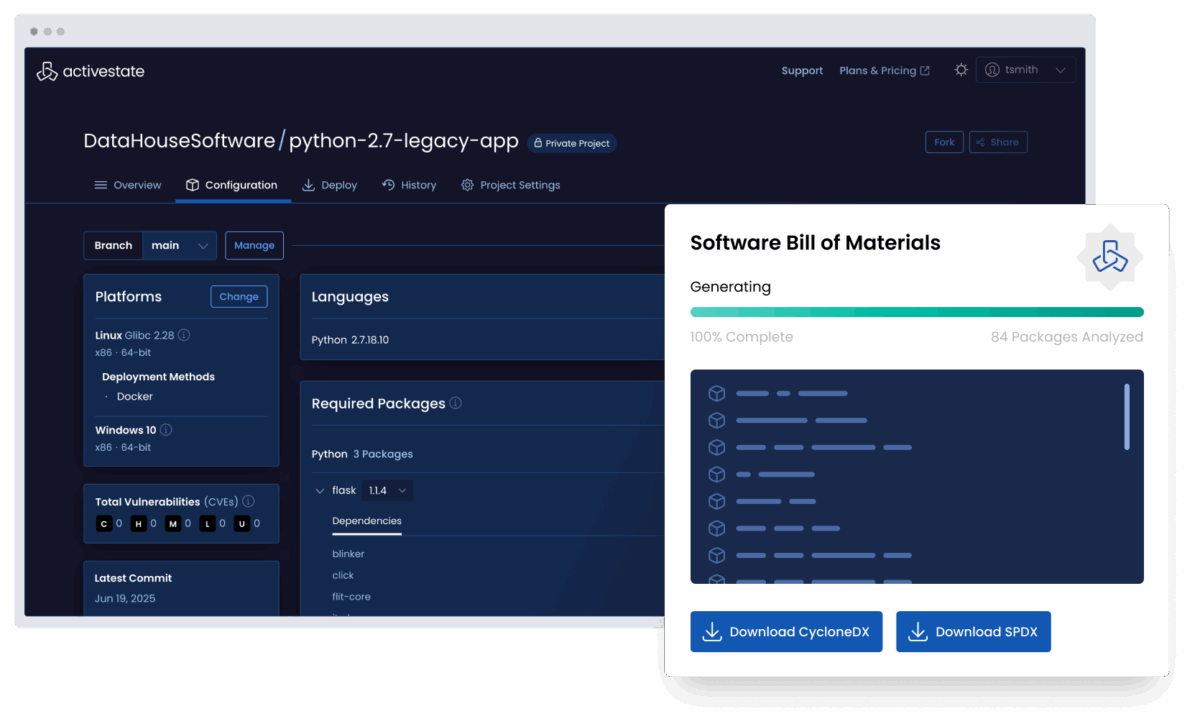
Maintain compliance with an SBOM-first approach
Generate and manage accurate SBOMs for legacy software to meet modern audit and regulatory standards.
Experience the ActiveState platform in action
See how end-of-life support becomes a secure, automated process.
In your personalized demo, we’ll show you how to:
- Build EOL versions from source just like modern packages
- Automate patching and remediation without breaking builds
- Create and maintain SBOMs to meet compliance needs
FAQs
What languages does ActiveState support beyond EOL?
We currently support a version of Python 2, legacy Perl, and Tcl, no longer actively maintained by the community. We however don’t support code branches that haven’t been maintained in decades.
Get in touch with a member of our product team to learn about the latest Python, Perl, and Tcl versions we support.
How does ActiveState apply security patches to outdated versions?
We use a secure, reproducible build system to validate patches from newer language versions, ensuring compatibility and stability.
Can I use ActiveState with my CI/CD pipeline?
Yes. The platform integrates directly into your existing toolkit so you can build, test, and deploy legacy code alongside modern software.
Will I still need to rewrite my legacy apps eventually?
Eventually, all code needs to evolve. But, the ActiveState platform gives you years of runway to plan migrations on your terms, without exposing your systems to open source vulnerabilities and unnecessary risk.
Explore more resources

How To Outsource Software Supply Chain Maintenance
Open source software supply chain maintenance is the new tech debt. Learn how to minimize its costs through outsourcing.
Unrestricted Upgrades for Python 2 Beyond End of Life
Mercury Financial discovered that ActiveState is the only company that has forked and continues to maintain a secure version of the Python 2 interpreter.

Best Practices: How To Update Your Codebase Without Breaking The Build
Most organizations never update their codebase for fear of breaking the build. Here's how to manage the risk and minimize the cost.



