Understand The True Extent of Your Open Source Vulnerabilities







Take advantage of 40M+ components and nearly 30 years of build expertise
Leverage the world’s most comprehensive open source database to uncover transitive dependencies, enforce security policies, and monitor vulnerabilities in real time.
ActiveState’s vulnerability blast radius transforms how your organization manages security posture, delivering deep insights that go far beyond basic CVE identification.
See beyond direct vulnerabilities
Most security tools only flag direct dependencies, leaving security teams blind to hidden transitive risks. The ActiveState platform maps your entire dependency graph, including hard-to-detect vulnerabilities that traditional Software Composition Analysis (SCA) tools miss.

Eliminate blind spots across your organization
Whether vulnerabilities are lurking in containers, CI/CD pipelines, or developer environments, the ActiveState platform provides a single, integrated view of open source risk, ensuring that security teams, developers, and DevOps teams are always aware of their attack surface.
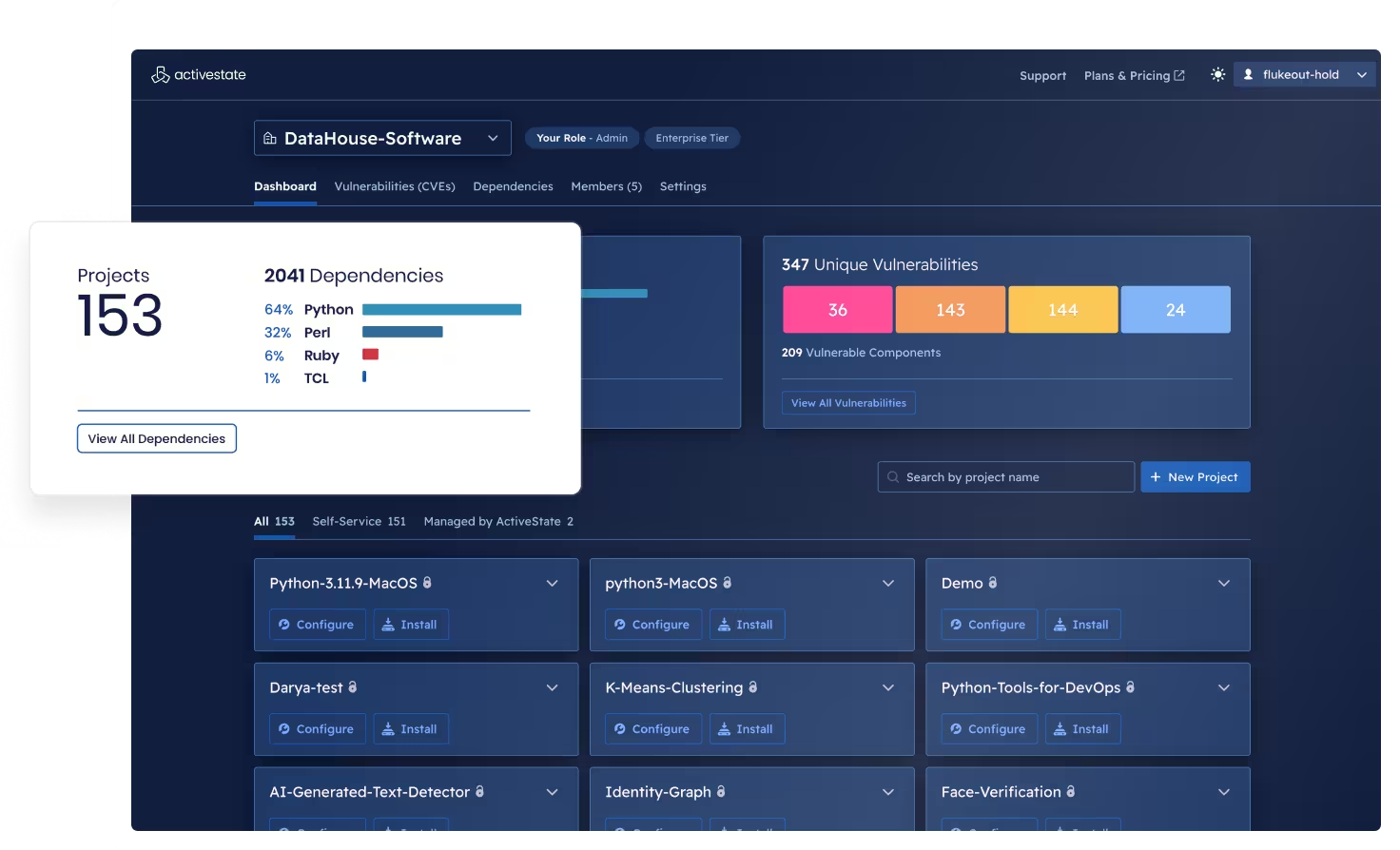
Gain access to the world’s largest open source component catalog
Featuring more than 40 million unique artifacts and nearly three decades of open source build expertise, the ActiveState platform is the world’s most comprehensive open source database, giving DevSecOps teams unmatched visibility into both direct and transitive dependencies.

Map, measure, and mitigate your open source risk
Traditional tools identify what’s vulnerable. ActiveState’s vulnerability blast radius allows you to see risk like never before, showing you why specific vulnerabilities matter, and how far the risk could spread.
Proprietary dependency intelligence
With an open source database of 40M+ unique artifacts and 25+ years of build expertise, our platform lets you uncover both direct and transitive dependencies, including those overlooked by standard SCA tools.
Organizational impact controls
Deploy universal package management and policy enforcement to ensure only sanctioned, secure open source components are used. Our advanced dependency resolution tools prevent risky and non-compliant packages from entering your software supply chain.
Continuous vulnerability monitoring
Stay ahead of emerging threats with runtime monitoring, comprehensive usage tracking, and crowdsourced insights that capture vulnerabilities in real time across all environments.
The ActiveState platform acts as your 24/7 sentry, alerting you to deviations from ideal configurations.
FAQs
How is the ActiveState platform different from traditional SCA tools?
Traditional SCA tools are reactive, only scanning for vulnerabilities after an application has been deployed. The ActiveState platform takes a preventative approach, and its vetted catalog of open source components helps block risky direct and transitive dependencies from entering your environment in the first place. It also digs deeper than most tools, analyzing down to the C library level to uncover issues others might miss.
What kind of organizations can benefit from the vulnerability blast radius capability?
Any organization managing open source at scale will benefit. It’s especially valuable in regulated industries, where you need to track the reach of vulnerabilities across your codebase and maintain a strong audit trail in order to comply with governmental and industry-specific policies and regulations.
Can ActiveState help with regulatory compliance?
Yes. The ActiveState platform provides a fully auditable history of every change. It also supports secure build environments and generates SBOMs and vulnerability reports to help you meet compliance standards, from FedRamp to NIST.
How does The ActiveState Platform prioritize vulnerabilities?
The ActiveState Platform prioritizes vulnerabilities by analyzing both the severity and reach of each open source vulnerability across your organization.
The platform shows which projects are affected, how widespread a vulnerability is, and what impact remediation will have to your application, including potential breaking changes. It also estimates the effort required to fix each issue, helping you focus on vulnerabilities that pose the greatest risk with the least disruption.
Why is ActiveState’s catalog larger than others in the space?
The ActiveState platform gives you access to the world’s most comprehensive open source component catalog, featuring more than 40 million unique artifacts and nearly three decades of open source build expertise.
Our catalog is larger than everyone else’s because it pulls from a broader range of ecosystems and keeps an immutable, historical record of every package created, including legacy packages that disappear from the internet. Moreover, our catalog is always growing in response to user’s needs thanks to a sophisticated system that is constantly ingesting from these ecosystems.
This means better visibility, reproducibility, and more comprehensive vulnerability coverage.
Empowering DevSecOps teams to secure their software supply chain
Knowing a vulnerability exists isn’t enough — you need to see its full impact. Find out how teams are using ActiveState’s vulnerability blast radius capability to secure their enterprise software supply chain without slowing down development timelines.




Experience ActiveState’s vulnerability blast radius in action
ActiveState’s vulnerability blast radius empowers DevSecOps teams with the deep insights needed to protect enterprise applications from hidden threats.
Stay one step ahead of your open source vulnerabilities

Why VMaaS Is Important for Your Enterprise Cybersecurity Strategy
ActiveState’s VMaaS solution delivers the last mile of vulnerability management through risk prioritization, precision remediation, and expert guidance. Here’s why it’s important to your enterprise cybersecurity strategy.

The 2025 State of Vulnerability Management and Remediation Report
Open source powers everything. Our latest report provides a candid look into how organizations manage vulnerabilities and remediation, and why traditional tools are no longer enough to tackle vulnerability remediation.

What is VMaaS? Understanding Vulnerability Management as a Service
Does it feel like your DevSecOps teams are constantly dodging cybersecurity threats? Explore why opting for security-as-a-service can help your team overcome these mounting challenges.



