Meet the Anaconda Alternative
Trusted by 97% of fortune 1000 companies.
Why do teams switch to ActiveState Python?
Support for any Python package
Get all packages built securely, on demand at no extra cost.
SBOMs and attestations included
Identify your dependencies, and verify their provenance and security.
Enterprise-wide Python visibility
Every package for each project in all environments in a single view.
What You Get With ActiveState Python
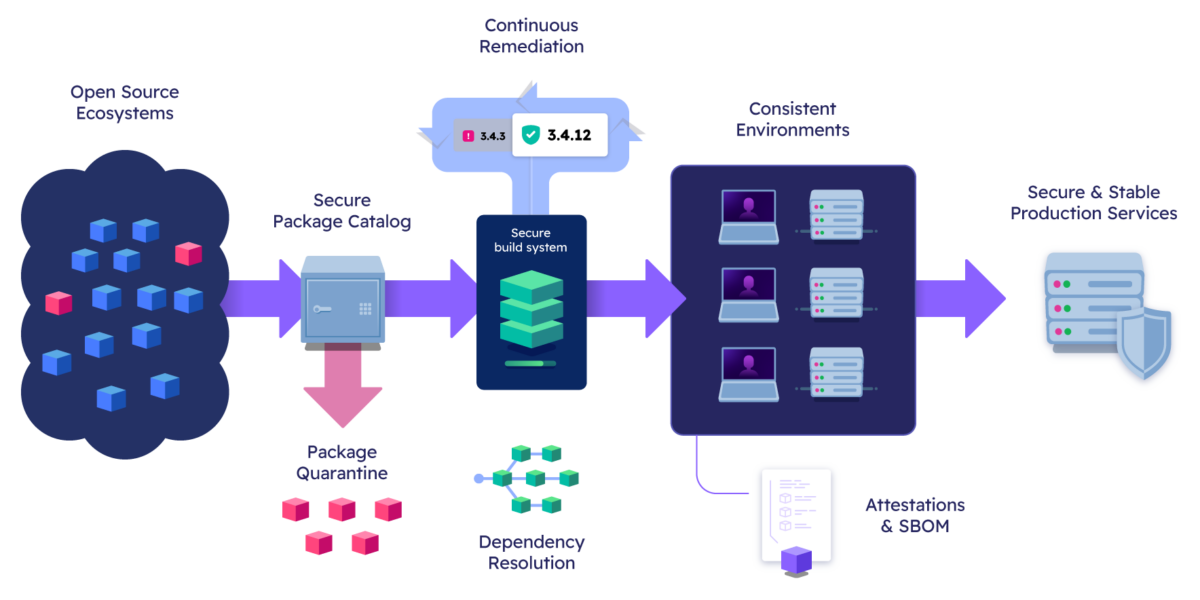
Secure Python Throughout the Build Process
The ActiveState platform builds Python packages from source automatically, no more risky PyPI or Conda downloads.
Want more? We got more.
Software Bill of Materials are provided at no extra cost, prove to everyone that your Python dependencies are secure.
All the Packages & Unlimited Python Distributions
Need more? We’ll grab and build it for you at no extra cost AND we support any number of distros within our platform.
So go ahead, build all you want without worrying about pricing blockers.
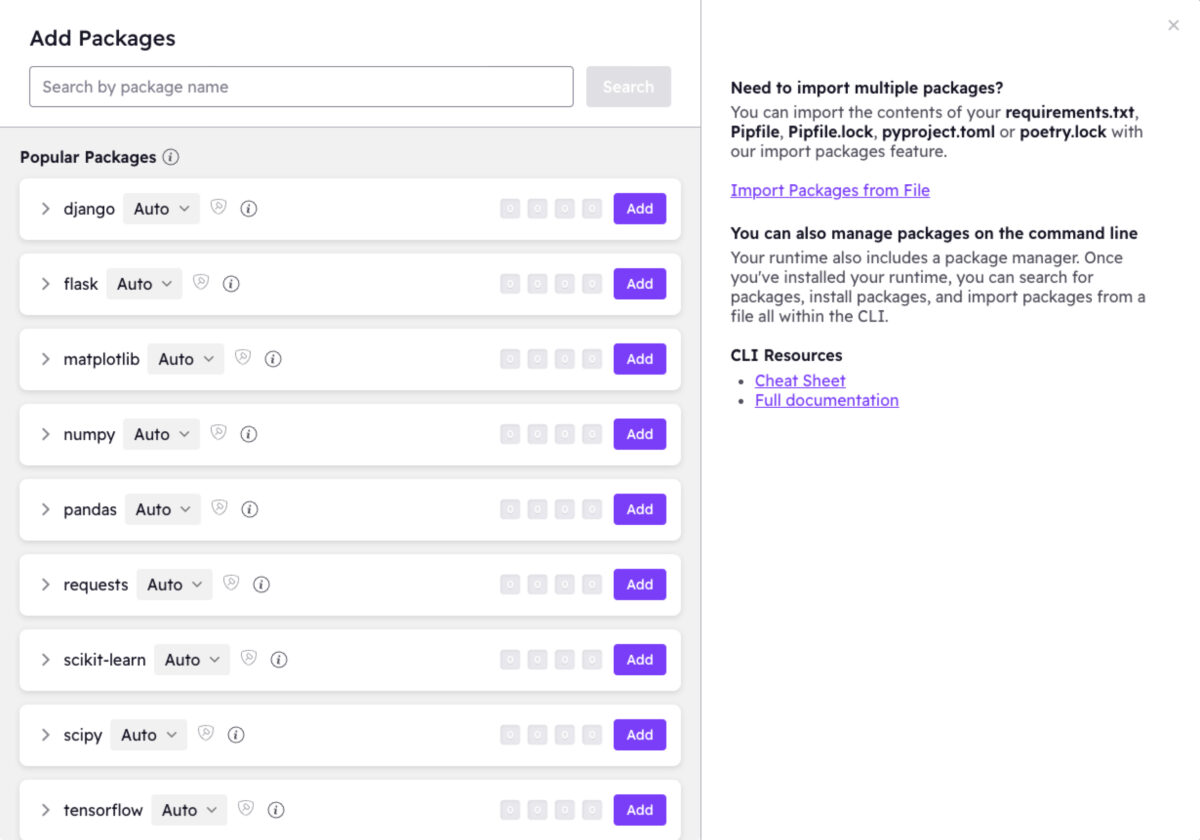
All-in-one Python Management Tool
“ActiveState is so seamless that the business can function even with turnover and little training. The lights stay on and our engineers don’t have to worry about what language they are using to add value.”

"I don't have to think too much about security and the complications anymore because ActiveState does it for me. At first I thought it was going impact my job but it just means I have more time to be strategic for the business."

Compare ActiveState vs Anaconda at a glance
| ActiveState | Anaconda | |
|---|---|---|
| Catalog | All Python dependencies found on PyPI | Limited + additional fee for non-standard dependencies |
| Catalog Updates | Continuous | Infrequent |
| Storage & CPU Costs | Included | Additional fee |
| SBOMs | Included | Additional fee |
| Provenance | Software Attestations included | Not Provided |
| Package Manager | State Tool | Conda |
| Package Builds | Automated via SLSA Build Level 3 hardened build service | Manually via Conda Forge |
| Virtual Environments | Automatically provisioned | Manually provisioned |
| Dependency Insight | Enterprise-wide roll-up view by user, project, CVE, etc | Per project view |
Got Questions? We’ve got answers
How easy is it to migrate from Anaconda to ActiveState?
Migrating from Anaconda to ActiveState is as simple as installing a version of ActiveState Python along with the State Tool. It’s very beginner friendly, read more about the simple 5 step migration process today.
Is ActiveState Python appropriate for Data Science, AI and ML?
ActiveState Python includes all of the Data Science, Machine Learning and Artificial Intelligence Packages, as well as popular Python libraries like Tensorflow, Pytorch, Numpy, Pandas, Syntax, Scipy, and Spyder typically used in academic and corporate projects. Historic and recent versions are included so users can take advantage of the latest features and innovations, while being able to reproduce older projects.
Can’t I just use community Python?
Of course you can, but downloading packages off PyPI is a risk. In the past year, 116 malicious installed packages were found in 53 projects. With software supply chain attacks growing, having a secure, constantly updated version of each Python package is not such a bad idea. ActiveState builds all packages from source ensuring security from the get-go for data scientists and developers alike.
Can I try ActiveState before purchasing?
Absolutely! Because ActiveState Python installs into a virtual environment by default, you can run both Anaconda Python and ActiveState Python side by side and compare their capabilities and key differences. Start by creating a free ActiveState platform account at https://platform.www.activestate.com/create-account.



