Software supply chain attacks have been happening for years, but have only recently achieved mainstream notoriety with the SolarWinds attack in December 2020. The reason for this is twofold:
- Reach: Tens of thousands of organizations were compromised by the SolarWinds attack, including US Government agencies that merely installed a signed software update from a trusted vendor.
- Impact: when a single cyberattack on an upstream vendor can compromise the entirety of the vendor’s customer base, the vendor must now be considered the front line of cyber security for all their customers.
As a result, software supply chain security must become a primary concern for software vendors, especially if they want to sell into the US Government, which has imposed a number of supply chain security requirements.
Software vendors looking to get a head start on implementing these kinds of software supply chain security requirements should consider the ActiveState Platform, which provides a turnkey, end-to-end secure supply chain solution for Python, Perl and Tcl. It fits with your existing software development processes, but imposes a number of controls to ensure the integrity and security of the open source components you import, build and run.
SolarWinds: Signed Software is No Guarantee of Security
Code signing has been around for decades, and is widely considered a best practice to ensure that code:
- Was created by the signing entity (typically, the author of the software)
- Has not been altered or corrupted since the code was signed
But the real value of signed code to most customers is the establishment of trust. Trusted software vendors are an essential ingredient in creating effective cybersecurity at any security conscious organization. Which is why the SolarWinds hack was especially pernicious: it effectively undermined trust in signed software.
Essentially, the attacker managed to compromise the build process of SolarWinds and insert a malicious DLL prior to the signing step. The infected DLL was then digitally signed and shipped to customers as part of a SolarWinds Orion platform update. Once installed, the malware acted as an HTTP backdoor, communicating with its command control server in order to obtain commands to execute.
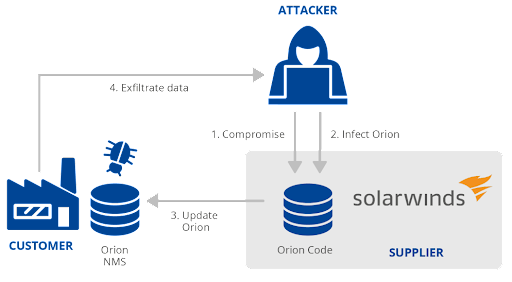
Image sourced from ENISA Threat Landscape
Additionally, since the compromised component was signed, it took longer for SolarWinds to discover the source of the hack. While it may be prudent to no longer put as much trust in signed code, having to verify every signed component across all your software development processes will severely slow you down. A better approach may be to ensure that individual development processes are secured from tampering.
Creating a Secure Software Build Process
Prior to the SolarWinds attack, software vendors have rarely considered their internal software development processes to be the target of hackers. But given recent trends, organizations should consider securing at least their software build processes as a first step.
For example, a recent attack on Codecov, a vendor of code management and audit solutions, also targeted the build service as the weakest link in the software development chain. In this case, attackers were able to obtain valid credentials from a poorly built Docker image, and then use them to compromise a bash script used by Codecov customers to upload their code. Once customers like IBM & HPE downloaded and executed this script, the attackers were able to exfiltrate data from them.
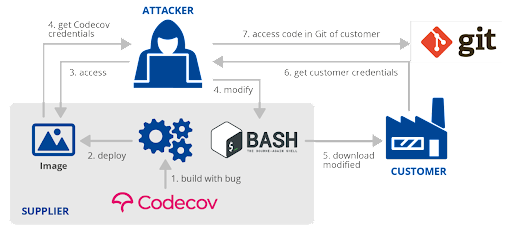
Image sourced from ENISA Threat Landscape
A secure build service starts with ensuring the security and integrity of the code you import. For example, in the case of open source components, best practices advocate importing only source code rather than prebuilt packages. Of course, working with prebuilt packages signed by a trusted vendor can provide an alternative to building everything from source, but security-conscious organizations may want to beware the cautionary tale of the SolarWinds case above.
Implementing the following controls can help ensure the integrity and security of your build process:
- Secure Build Service – a dedicated service that runs on a minimal set of predefined, locked down resources rather than a developer’s desktop or other arbitrary system that can offer a larger attack surface to hackers.
- Scripted Builds – use predefined build scripts that cannot be accessed and modified within your build service in order to prevent exploits.
- Ephemeral, Isolated Build Steps – ensure that every step in a build process executes in it’s own container, which is discarded at the completion of each step. In other words, containers are purpose-built to perform a single function, decreasing the potential attack surface.
- Hermetic Environments – ensure that there is no network access provisioned for the container in each build step. This prevents dynamic packages from including remote resources.
Implemented correctly, the result should be verifiably reproducible builds, which are builds that not only produce the same bits every time given the same inputs, but whose provenance can also be verified by tracing each component back to its original source code.
Conclusions: Secure Your Software Development Processes
The software supply chain, which spans the importing, building and running of code, can only ever be as secure as its weakest link. For organizations that take security seriously, there are a number of frameworks that can help ensure the security and integrity of these software processes, including:
- The US Government’s National Institute of Standards and Technology (NIST), which provides guidelines that help define a Secure Software Development Framework (SSDF).
- Google SLSA, which provides a set of controls that can help ensure the integrity and security of software code/components that are imported, built and consumed during the software development process.
That said, implementing a framework like SLSA or SSDF can be both time and resource intensive. For those software vendors looking for a headstart securing their supply chain, the ActiveState Platform provides a turnkey supply chain security service that’s quick to implement, easy to use and highly automated. Rather than cobbling together custom code and a number of point solutions from multiple vendors, the ActiveState Platform can provide an out-of-the-box, end-to-end solution saving organizations considerable time, resources and money.
Next steps
- Watch our webinar on ‘Securing Your Python, Perl and Tcl Supply Chains’
- Sign up for a free account and try the ActiveState Platform for yourself