US President Biden has called for bold software changes as a response to the dramatic rise in cyber attacks, including some of the most crippling hacks to both physical and software infrastructure in recent memory:
- SolarWinds, which compromised IT resource management software used by over 33,000 clients, including the US Government
- Colonial Pipeline, which crippled delivery of gas and oil to the US East Coast
The President’s Executive Order calls for adoption of multiple security best practices, but of special note to software and FedRAMP vendors is the fact that the US Federal Government will now require:
- A software Bill Of Materials (BOM) associated with any software purchased by the government
- A way to check for and automate vulnerability remediation
- Provenance, or the ability to be able to identify the origin for all software components
For software and FedRAMP vendors hoping to sell their applications and solutions to US Federal Government agencies, these requirements may pose a significant barrier to entry. And what the Federal Government initiates, the private sector is likely to adopt. ActiveState is here to help.
The ActiveState Platform is a universal package management solution for Python, Perl and Tcl (more programming languages coming) that helps ensure secure open source components are used from development through to production. More pertinently, it also delivers many of the supply chain security features required by President Biden’s Executive Order.
Software Bill of Materials
The Executive Order calls for “providing a purchaser a Software Bill of Materials (SBOM) for each product directly or by publishing it on a public website”.
I’ve discussed BOMs previously, but to recap, a BOM is simply a comprehensive list of ingredients required to build your application. A BOM can include:
- A version of the programming language
- Open source packages from the language’s ecosystem, as well as their dependencies
- Operating system (OS)-level dependencies
- Proprietary code packages (ie., code your developers have written)
- Configurations (ie., metadata like version number, open source license, etc)
- A Common Vulnerabilities and Exposures (CVE) report, showing vulnerabilities for each component
The ActiveState Platform goes a step further in providing you with both:
- Python, Perl and Tcl transitive dependencies (ie., dependencies of dependencies)
- Shared dependencies (ie., OpenSSL, which is shared across all the operating systems your application supports)
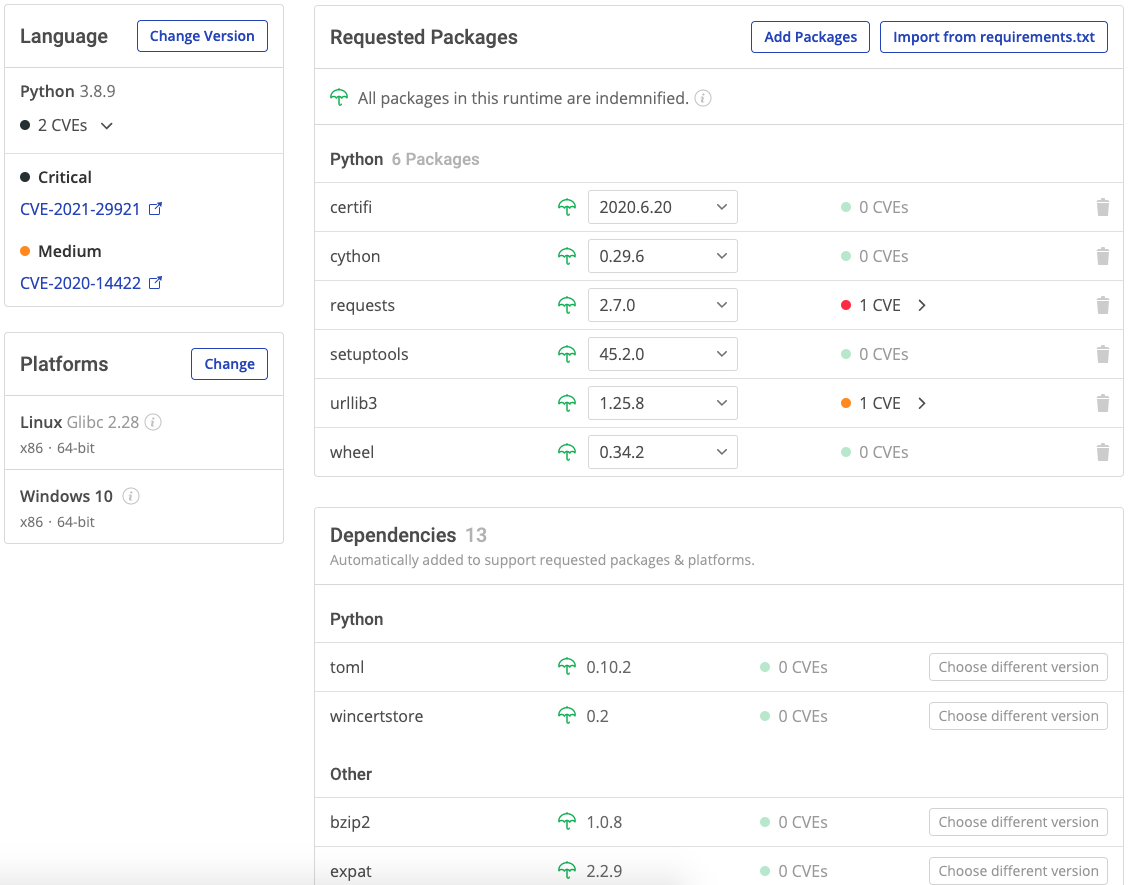
In accordance with the Executive Order, you can make your BOM available directly from the ActiveState Platform by simply copying and exporting it (for private projects), or else providing a link to it (for public projects). A typical BOM might look like the following:
The BOM not only identifies all packages and dependencies, but also which ones have CVEs, as well as links to the National Vulnerability Database that explain each in detail.
Open Source Vulnerability Remediation
The Executive Order calls for “employing automated tools, or comparable processes, that check for known and potential vulnerabilities and remediate them”.
I’ve discussed the vulnerability remediation capabilities of the ActiveState Platform before, as well. To recap, the ActiveState Platform provides you with:
- Status updates when your Python, Perl or Tcl environment is vulnerable
- A PDF report showing the severity level and details for each vulnerability
- The ability to fix and automatically rebuild your environment with secure components in minutes
Because the ActiveState Platform tracks multiple versions of all your components, you can remediate vulnerabilities at the OS, package and dependency level by simply selecting a non-vulnerable version. The ActiveState Platform can save considerable time and effort by automatically rebuilding your environment, ready to be pulled into your CI/CD pipeline for testing.
Software Code Provenance
When it comes to provenance, the Executive Order calls for “maintaining accurate and up-to-date data, provenance (i.e., origin) of software code or components” as well as “ensuring and attesting, to the extent practicable, to the integrity and provenance of open source software”
Here, the ActiveState Platform provides you with:
- A Select Catalog – All our Python, Perl and Tcl packages are imported from their respective official repositories (PyPI, CPAN, etc), as well as others sources (such as GitHub).
- Builds from Source – All packages are automatically built from source code for Windows, Linux and macOS in just a few minutes, rather than relying on pre-built binaries which may contain malicious code.
- Indemnified Builds – Our enterprise customers have the ability to create Python, Perl and Tcl environments from components that have been vetted by ActiveState and found to be well maintained and suitable for inclusion in commercial applications. You can see an example of just such an indemnified build in the screenshot above.
- Audit Trail – all changes to your Python, Perl and Tcl environments are tracked so you can always identify who made which changes, when.
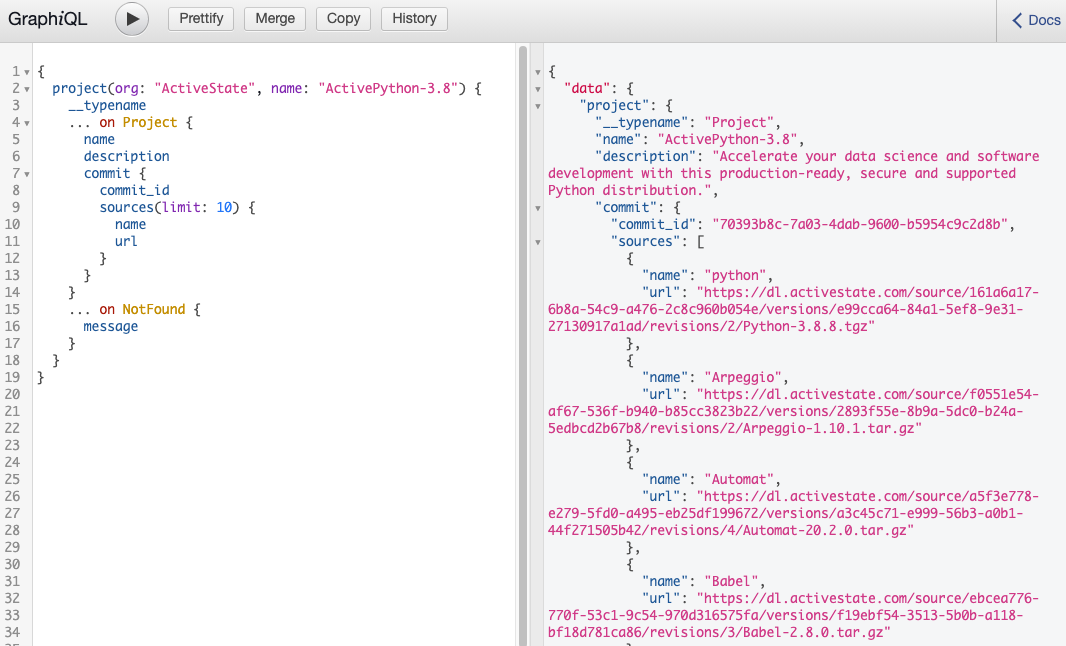
You can even use the ActiveState Platform’s Build Graph API to verify the source code for each package in your environment. For example, running an API query will return links to the source code for our ActivePython project:
Conclusions: Shift Security Left
When the President of the United States puts open source security in front of issues like the pandemic, global warming, and the economy, the status quo is no longer tenable and new solutions need to be explored.
Perhaps the most telling issue is the fact that the SolarWinds hack compromised the company’s development environment (rather than the usual production environment hack), meaning that any software they created would be compromised. This is the harbinger of a new breed of attacks that target far up the food chain–something that DevSecOps proponents have been warning us about for years: the need to shift security left to ensure the code you develop with is secure.
This is the focus of the ActiveState Platform, which allows you to not only create secure Python, Perl and Tcl environments with which to build your applications, but also ensure they stay secure and up-to-date over time in a simple, automated way.
Ready to see for yourself? You can try the ActiveState Platform by signing up for a free account. Or sign up for a free demo and let us show you how you can secure the open source supply chain at your organization.
Need more information about securing your software? Read these: