Secure Environment Management
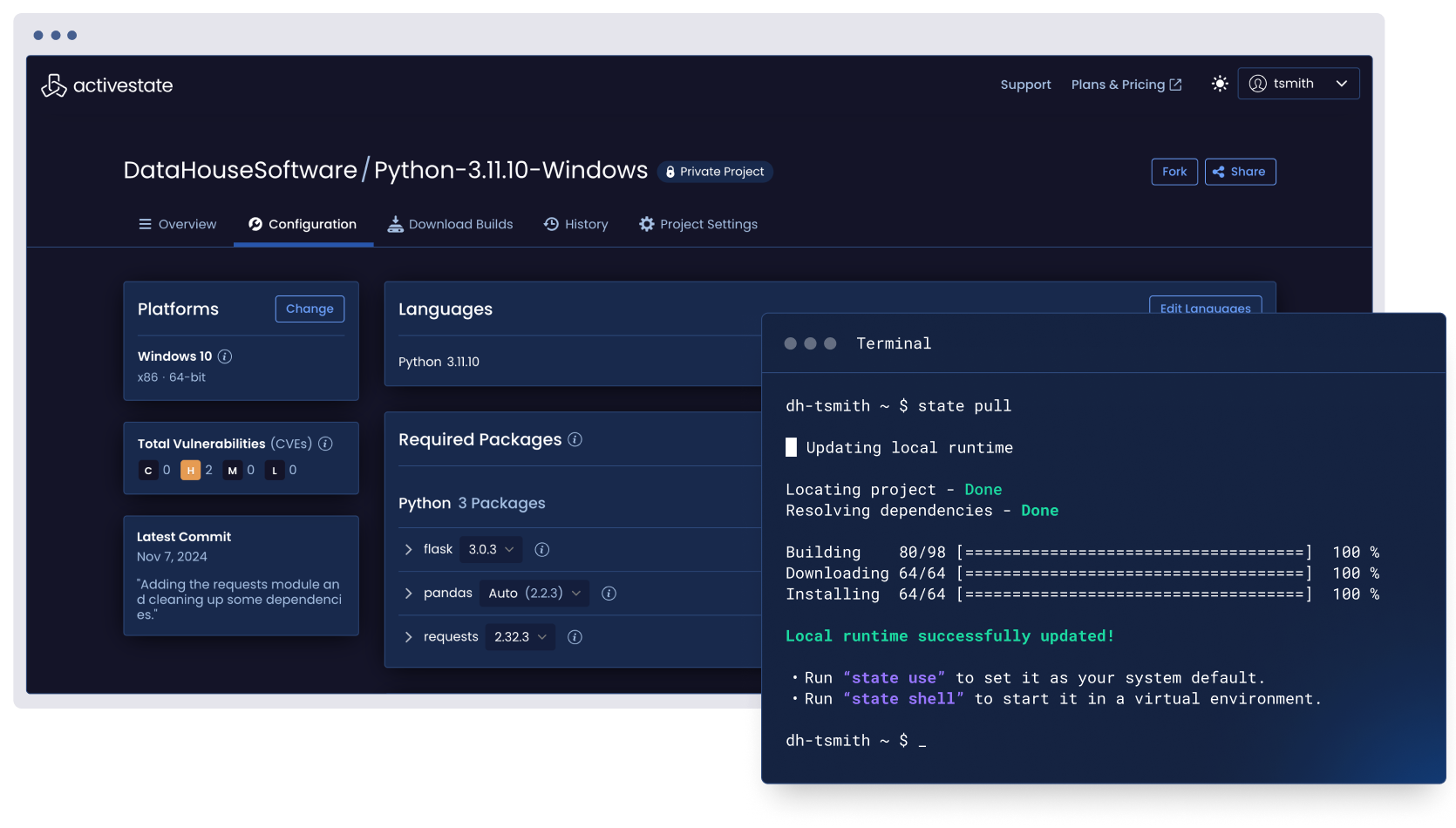







Challenges with secure environment management
Without a reproducible build system, environment configuration issues arise within and between teams, slowing down software delivery and deployment, or even resulting in production rollbacks.
ActiveState speeds time-to-market, eliminating missed revenue opportunities. For a large enterprise, even a delay that impacts 1% of deals can mean millions of dollars in lost revenue.
Tracking and fixing configuration drift between environments when every developer is installing their own packages on their machine is complex, time-consuming, and frustrating – leaving you playing your own sort of whack-a-mole.
With ActiveState, all developers make use of the same development environment, eliminating the “works on my machine phenomenon” to let you control the chaos, reduce drift, and save time and money.
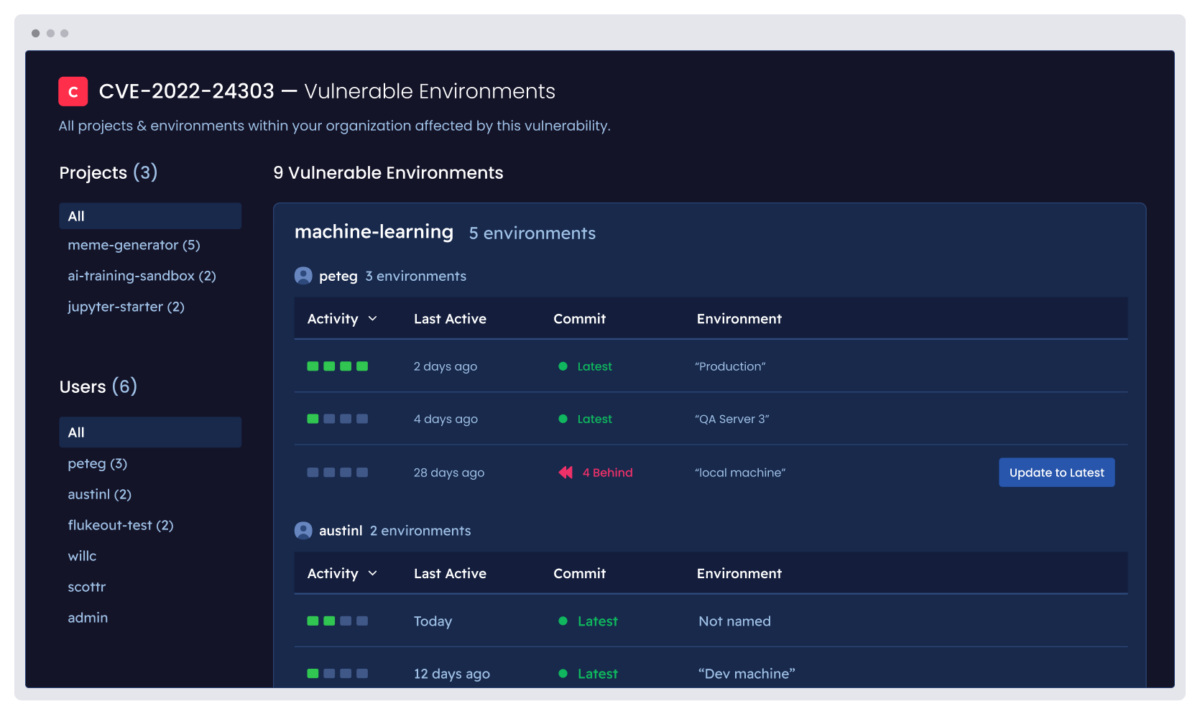
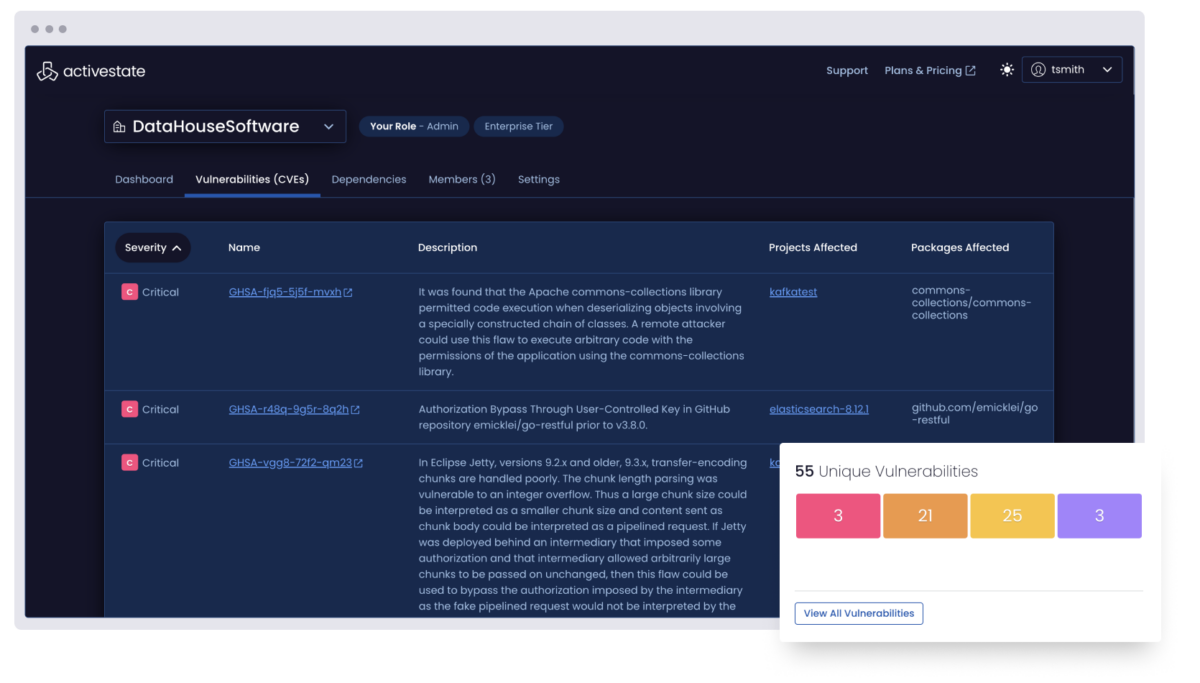
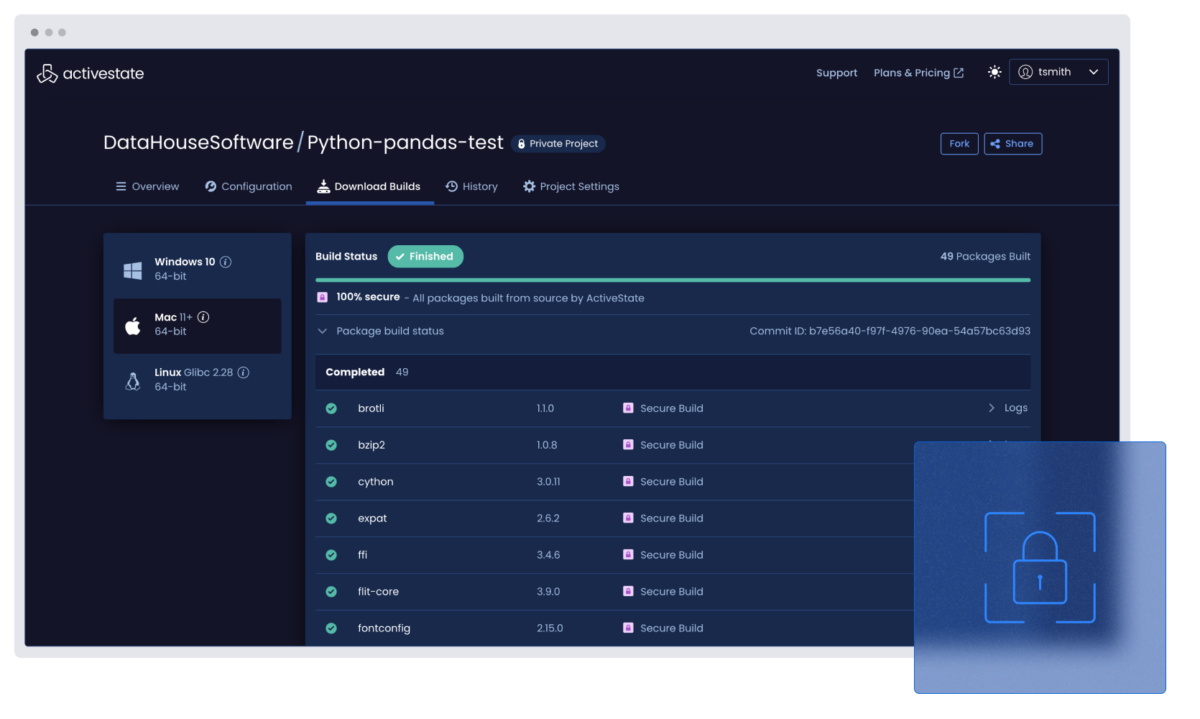
Security risks increase when vulnerabilities are not patched uniformly across all environments. Worse, inconsistent sets of dependencies across environments may leave you unaware of which environments are even exposed to attack.
ActiveState’s consistent environments enable you to be less susceptible to security breaches, deflecting as much as $4.88M per incident, as well as mitigating reputational damage.
The ActiveState difference
With ActiveState’s SLSA3-compliant automated universal build system you can deliver consistent development, test, and production environments across your organization. This improves adherence to corporate standards and policies, speeding the time to uniformly updating vulnerabilities across environments, reducing alerts and speeding up CI/CD cycles, and minimizing config errors that require production rollbacks.