ActiveState has a 20+ year history of making open source software easier to use for developers and easier to adopt by enterprises. While these two principles are still true, the ActiveState Platform enables far more use cases beyond just providing organizations with open source language distributions, including:
- Governance – how do you ensure that teams work only with a pre-approved set of open source components while ensuring those components are up-to-date?
- Observability – how can you create a comprehensive catalog of open source components deployed in each project across the extended enterprise?
- Remediating Vulnerabilities – how can you quickly and easily harden container-deployed applications to meet SLAs?
Many of these use cases can be addressed by combining point solutions that enterprises have already implemented, but cobbling together multiple solutions to solve a use case adds cost and complexity. By contrast, ActiveState provides the same capabilities with a single solution, the ActiveState Platform, delivering secure, working code faster. Let’s dig in.
Key Open Source Use Cases
Open source software typically comprises >80% of any codebase, which means an average of ~520 open source components per application. Managing and updating open source at this kind of scale for any existing application is often the equivalent of trying to change the tires on a bus as it’s rolling. The following are the top three use cases we help our customers with so their development processes don’t get derailed on the way to production.
Use Case #1 – Open Source Governance
Governance is a catch-all term, but the main concern for most organizations is control: how can I ensure that the right groups are working with the right set of approved open source components? And just as important, how can I make sure those components are fit for use?
Today, most organizations use an artifact repository to collect and create a “golden set of blessed components.” The problem with this approach is the static nature of repositories, which forces organizations to be reactive. But adding a new component (or even a new version of an existing component, which might happen when a vulnerability is discovered) can mean weeks of waiting for security, compliance and R&D teams to sign off, impacting release dates, which is unacceptable. As a result:
- 2.1B dependencies with known vulnerabilities were downloaded in both 2022 and 2023 despite the fact that there was a non-vulnerable version available.
- 81% of organizations admit to shipping applications with known vulnerabilities.
In contrast, the ActiveState Platform provides a continually updated catalog of open source components, enabling stakeholders from dev, security, and compliance to be proactive about identifying and approving new dependencies or new versions of dependencies.
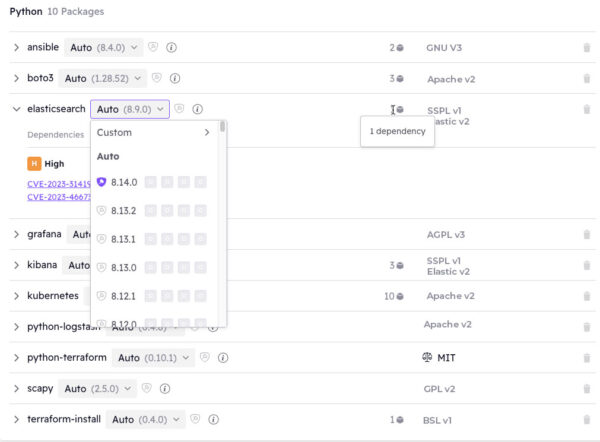
For example, the screenshot below is typical of too many organizations who become stuck on an outdated, vulnerable version of a dependency. In this case, ActiveState’s catalog shows a number of newer versions of elasticsearch have been released (along with the license and security status) that can be used to eliminate the vulnerabilities in the present version:
Figure 1 – ActiveState’s continuously updated open source catalog
The ActiveState Platform provides a single, central source of truth for all stakeholders, fostering collaboration between development, security and compliance teams and removing bottlenecks to dependency approval. The result is enhanced security and reduced risks associated with open source software, ensuring compliance and safe adoption practices.
Use Case #2 – Open Source Observability
Observability, or more commonly discoverability is based on the ability to identify all open source software in use across the extended enterprise, including:
- What version of which components are currently in use?
- What is their vulnerability and license profile?
- Where are the components deployed?
Such a comprehensive profile would simplify the task of identifying and remediating risk.
Today, most organizations employ some kind of Software Composition Analysis (SCA) tool to scan their artifact repositories and existing applications in order to create a comprehensive catalog of open source dependencies.
The problem with this approach is twofold:
- Most open source software is imported as prebuilt binaries rather than source code.
- Organizations may or may not have access to the source code for the applications they have deployed.
As a result, SCA tools employ a binary scanner to essentially reverse engineer a list of open source components from compiled sources. Depending on the scanner’s capabilities, the generated list may or may not be complete, which is why most organizations deploy multiple SCA tools. This is why Application Security Posture Management (ASPM) has gained momentum in recent years, because it allows for results to be combined in a single dashboard to help organizations resolve discrepancies.
Rather than purchasing and managing multiple point solutions, the ActiveState Platform takes a different approach. By automatically building all open source dependencies (including OS-specific binaries) securely from vetted source code, organizations are assured of getting a comprehensive list of components (including build dependencies, as well) using a single, holistic solution that identifies:
- Dependency version
- Dependency vulnerability status
- Dependency license(s)
- Project/ deployment for each dependency
For example, the following screenshot shows dependencies by vulnerability status:
Figure 2 – ActiveState Dashboard: Vuln’s by Dependency
The dashboard can be used to identify which projects contain which dependencies, as well as understand how widespread a specific vulnerability may be. Clicking on a project will allow you to identify the development team, along with their email addresses. As such, it becomes a simple process to notify them and track their response.
By generating a definitive manifest of all dependencies no matter the programming language or operating system (and even including build dependencies) in a single platform, ActiveState lets organizations not only save time and resources managing multiple point solutions, but also improves risk management.
Use Case #3 – Container Hardening
Organizations that deploy container-based applications understand the pain of trying to track and keep them all up to date, especially in a regulated industry with aggressive SLAs for remediation of high risk elements, such as Known Exploited Vulnerabilities (KEVs). For example, some critical US government KEVs can have as little as a 4 day SLA.
Today, organizations primarily make use of container scanners to determine:
- What’s deployed in containers?
- The open source component manifest for each container
- Current vulnerability status of each component
Unfortunately, container scanners suffer from many of the same problems that binary scanners exhibit, as discussed in Use Case #2 above. They are generally good at identifying the open source software that’s deployed (i.e., Apache Airflow, nginx, ELK stack, etc), but they struggle with creating a complete inventory of open source dependencies. And while they can notify you when updated versions become available that address vulnerabilities, they leave the hardening of the container to you. All of which can make vulnerability remediation for container-based applications difficult to do at scale in a timely manner.
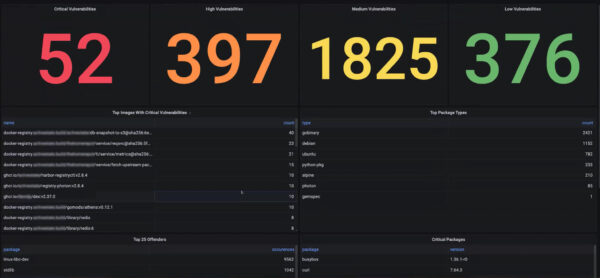
Figure 3 – Trivy Report: Vulnerabilities proliferate in containers
Because ActiveState can automatically build open source securely from vetted source code and package it in a container, you can decrease Mean Time To Remediation (MTTR) by updating vulnerable components quicker. For example, if a vulnerability is identified with Apache Airflow, rather than waiting for an upstream patch to be released by Apache, ActiveState can patch the affected downstream component and rebuild a non-vulnerable version of Airflow to meet SLAs sooner.
As a result, organizations can remediate vulnerabilities quicker in order to better meet SLAs, while enhancing application security and performance.
Conclusions
The speed of software development is a difficult task master, forcing organizations to adopt tools that automate many of the processes that would otherwise become bottlenecks on the way to release. But while those tools do relieve a specific pain, they can also result in the creation of poor open source management practices that impact the overall quality of the software, effectively trading one limitation for another. And the more tools you implement, the greater the management overhead, which can add costs and complexity to your development processes.
Instead, consider implementing a single platform that can automatically resolve multiple issues without slowing you down. When that platform is provided by a vendor that can partner with you to ensure open source security while removing complexity throughout your software development lifecycle – from source code to production to maintenance – it allows you to secure your software supply chain and proactively manage risk.
Next Steps
Read more about how our customers are taking advantage of the ActiveState Platform to tame open source software complexity.