Quick Reads
All Quick Reads
Top Benefits of Software Supply Chain Security Tools
The Secure Curated Catalog Advantage In the modern software supply chain, the risk isn’t just in how you build software, but in what you build ...
Read More
Getting Started with ActiveState: Secure Your Open Source Software Supply Chain
Three steps to discover, observe and remediate OSS.
Read More
How to Secure Machine Learning Environments
What is Cloudera and Cloudera Machine Learning? Cloudera specializes in data management by offering a comprehensive platform for big data and analytics that includes various ...
Read More
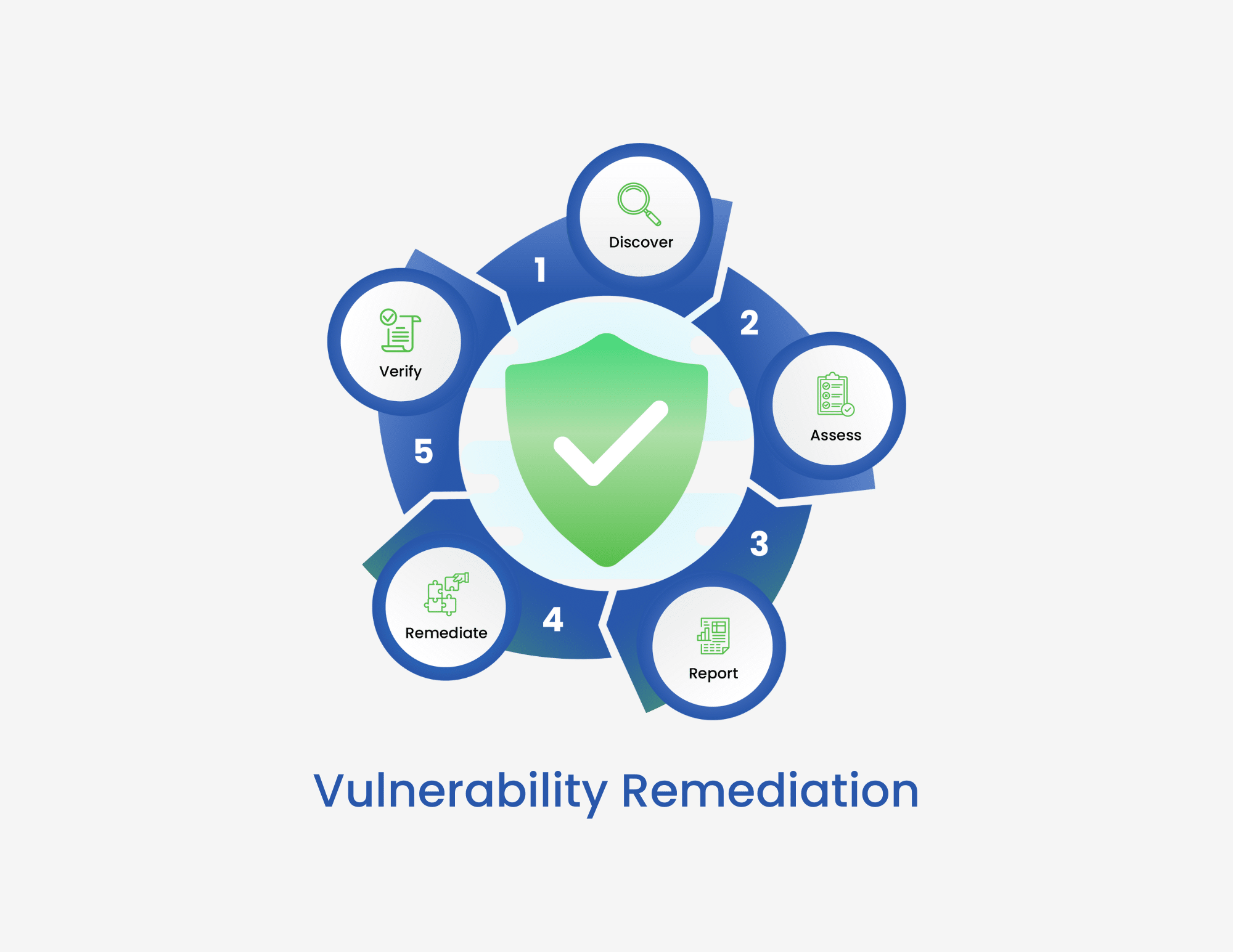
The Complete Guide to Vulnerability Remediation for DevSecOps Teams
Learn what vulnerability remediation is and how it is a key step in ensuring the security and integrity of your applications.
Read More
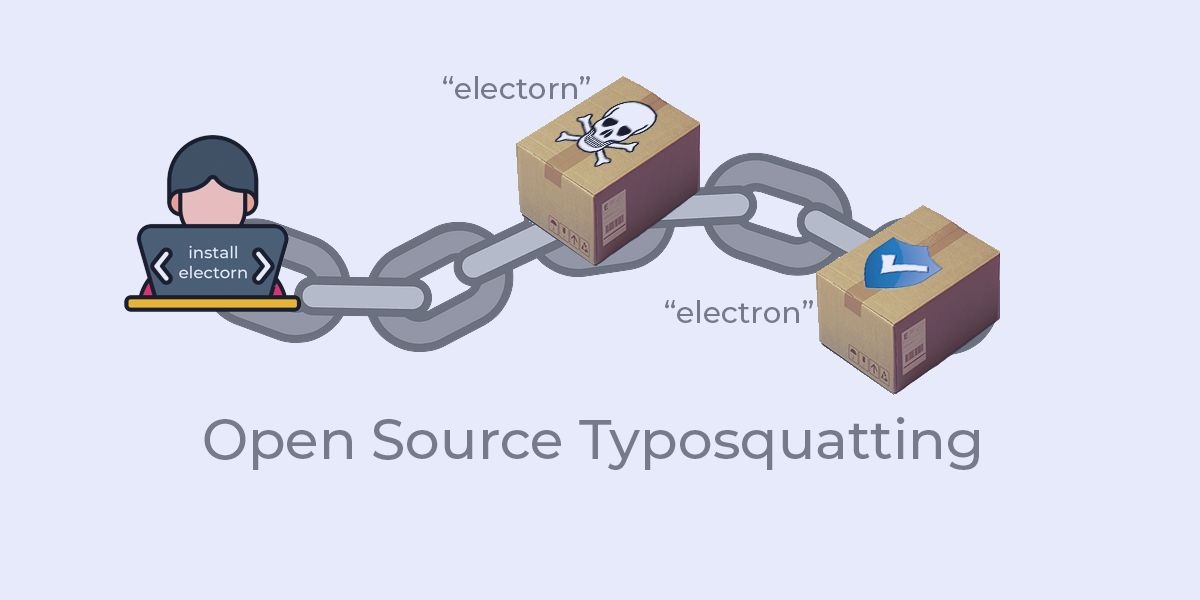
How Open Source Typosquatting Attacks Work
Learn how typosquatting works by exploiting popular packages and why it is the most popular form of cyberattack.
Read More
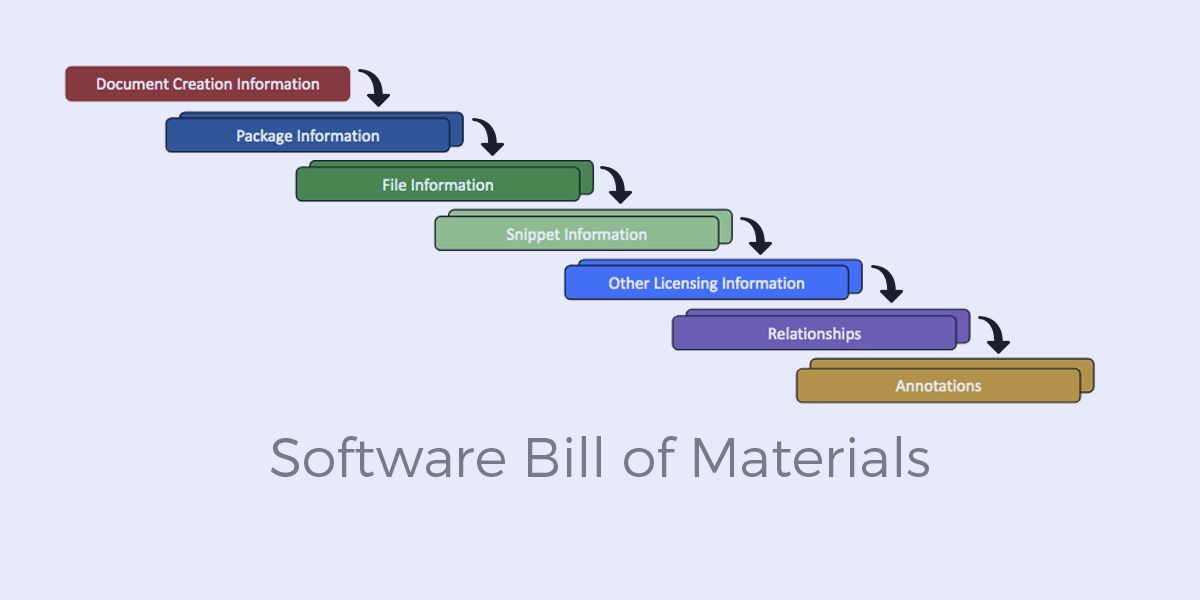
Software Bill of Materials (SBOMs)
Learn what a software bill of materials is and how it can help you secure your development processes
Read More
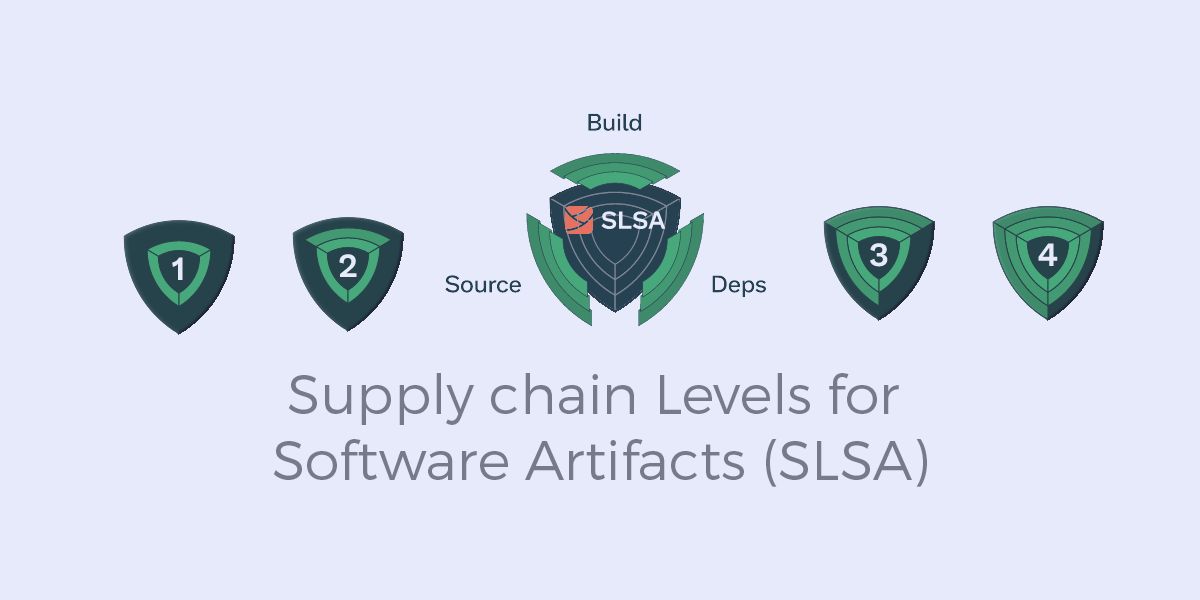
Supply Chain Levels for Software Artifacts (SLSA)
Learn what the SLSA security framework is and how you can use it.
Read More
Dependency Confusion
Learn what a dependency confusion attack consists of, how to identify it and how to protect your software from it.
Read More
Software Supply Chain Threats
Learn about the top 3 most prevalent software supply chain threats.
Read More
Software Supply Chain Security
Click to learn about software supply chain security, identifying and remediating risks of an organization’s software.
Read More
Dependency Management with Pip, Python’s Package Manager
Learn how to manage dependencies with Pip in conjunction with a requirements.txt file, which allows for the pinning of packages and their dependencies to specific ...
Read More