Open Source Software (OSS), while widely adopted for its flexibility and cost-effectiveness, increases security risks due to the extensive use of third-party libraries that may harbor hidden vulnerabilities. Yet, 96% of applications rely on it. Managing security is challenging and time-consuming, so it’s no surprise that 81% of developers admit to shipping software they knew had vulnerabilities.
Neglecting to secure the open source software supply chain can lead to costly breaches and compromised trust, making proactive vulnerability management essential.
Get everything you need to secure your open source software supply chain in one unified platform. ActiveState empowers you to discover dependencies, assess vulnerabilities, streamline remediations, and maintain trusted builds automatically.
Here’s how to get started:
Step 1 – Scan For OSS
ActiveState will identify the vulnerabilities & dependencies in all your projects, no matter where they’re deployed. For this trial, you can:
- Test it out using our secure sandbox environment
- Or contact our open source experts to scan your own Kubernetes clusters and other environments.
Step 2: Gain Insights into Open Source Vulnerabilities and Dependencies
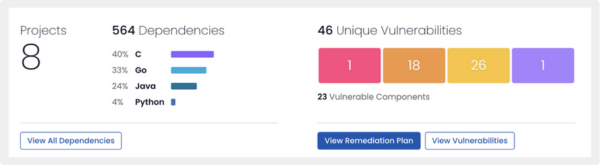
View vulnerabilities & dependencies on your dashboard to gain a comprehensive understanding of your software components.
ActiveState identifies all top-level dependencies, transitive dependencies and OS-level libraries along with their version, and generates detailed reports that highlight the vulnerability status for each, where the vulnerable components are deployed, and maps their complex relationships, allowing you to address risks before they become problems.
<View Your Vulnerabilities& Dependencies>
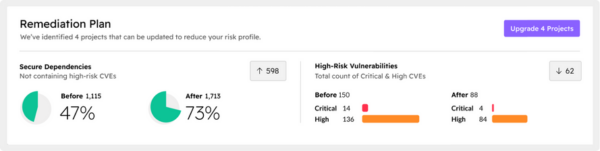
Step 3: Take Action with the Intelligent Remediation Plan
Next, explore the remediation plan, which can help you address those critical and high-severity vulnerabilities that have a fixed version available.
Because we continuously update our catalog of open source software from community repositories, we are able to identify whether an upstream vulnerability fix (i.e., application-level fix) already exists, or whether a fixed version only exists for individual vulnerable components at this point in time.
Given the severity of the vulnerability, its prevalence among your projects, and whether the upgrade target is a minor or major version, , you’ll be able to make informed decisions about how best to prioritize addressing security risk.
Upgrade impact reports provide a clear picture of how potential changes could impact you, helping you balance the risk of taking an update against the stability of your applications.
Next Step: Connect Your Environment
Ready to see ActiveState in action with your own data? Talk to our experts today to test out ActiveState for free in your environment.