End-to-End Software Supply Chain Security Platform
Prove you follow secure software practices across the org.
Help security and compliance teams track and audit your software.
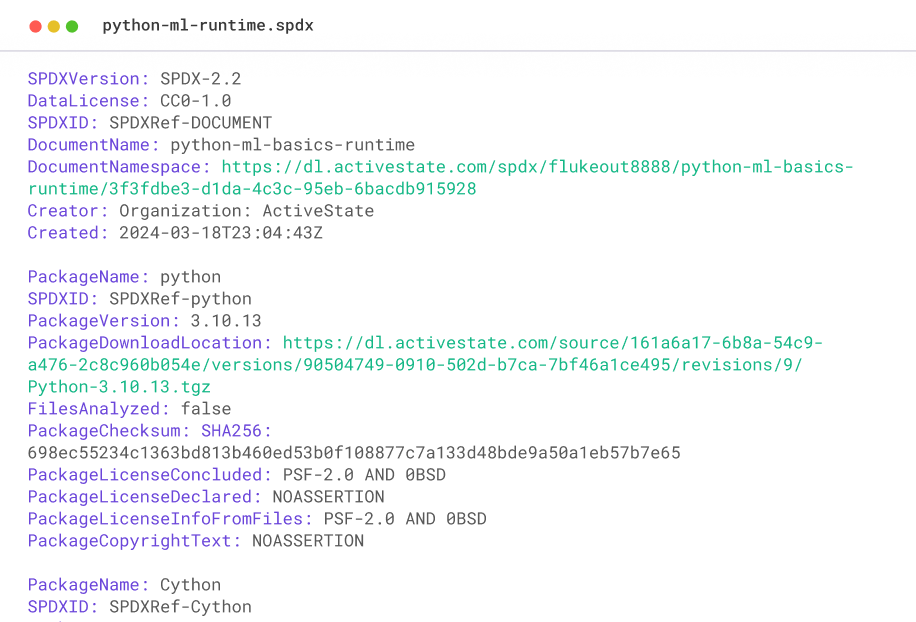
Create and verify Software Bill of Materials (SBOMs) throughout your SDLC with ActiveState for all open source runtime environments, including per dependency metadata like licenses, suppliers and versions.
Save your developers time remediating vulnerabilities.
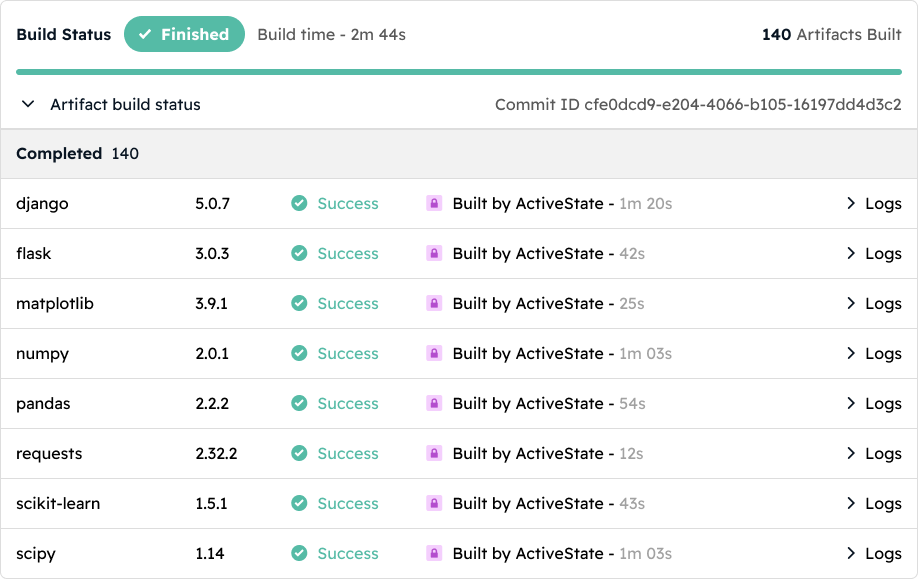
Speed up remediation by decreasing both Mean Time To Remediation (MTTR) with automated runtime rebuilds and Mean Time To Detection (MTTD) of vulnerabilities with notifications.





Read the latest on Government Policies
Learn more about how ISVs who serve governments and the public sector can meet CISA attestation requirements.
Get to know the Secure Software Development Framework (SSDF) and how to streamline adoption.
Automate SSDF Requirements and CISA Attestation Compliance
Meet these 4 requirements with ActiveState to deliver your code quickly and securely.
REQUIREMENT #1
Secure Environments
It all comes down to minimizing the risk of attack vectors being exploited. How hardened are your environments?
Hardened software development environments let you avoid being reactive when new vectors of attack emerge. ActiveState lets you get ahead of the game.
REQUIREMENT #2
Software Supply Chain Security
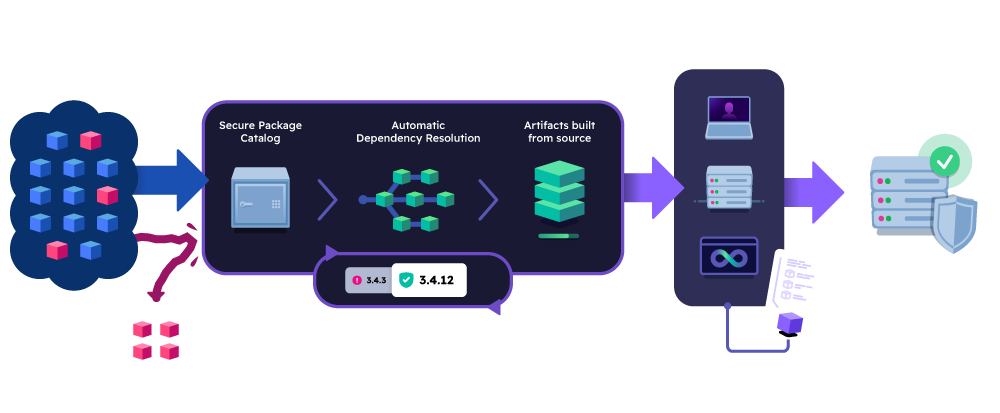
Reliance on binary scanners can be problematic, resulting in far too many alerts and ultimately alert fatigue. But what’s the alternative?
The only way to be proactive about software supply chain security is to build open source components from source code. ActiveState lets you automate it with zero effort.
REQUIREMENT #3
Provenance
Establish trust by offering a way to independently validate the security and integrity of your applications.
Software attestations are key to proving open source is acquired from a legitimate source, built in a secure manner, and not tampered with. ActiveState provides both Provenance and Verifiable Summary Attestations (VSA).
REQUIREMENT #4
Vulnerability Remediation
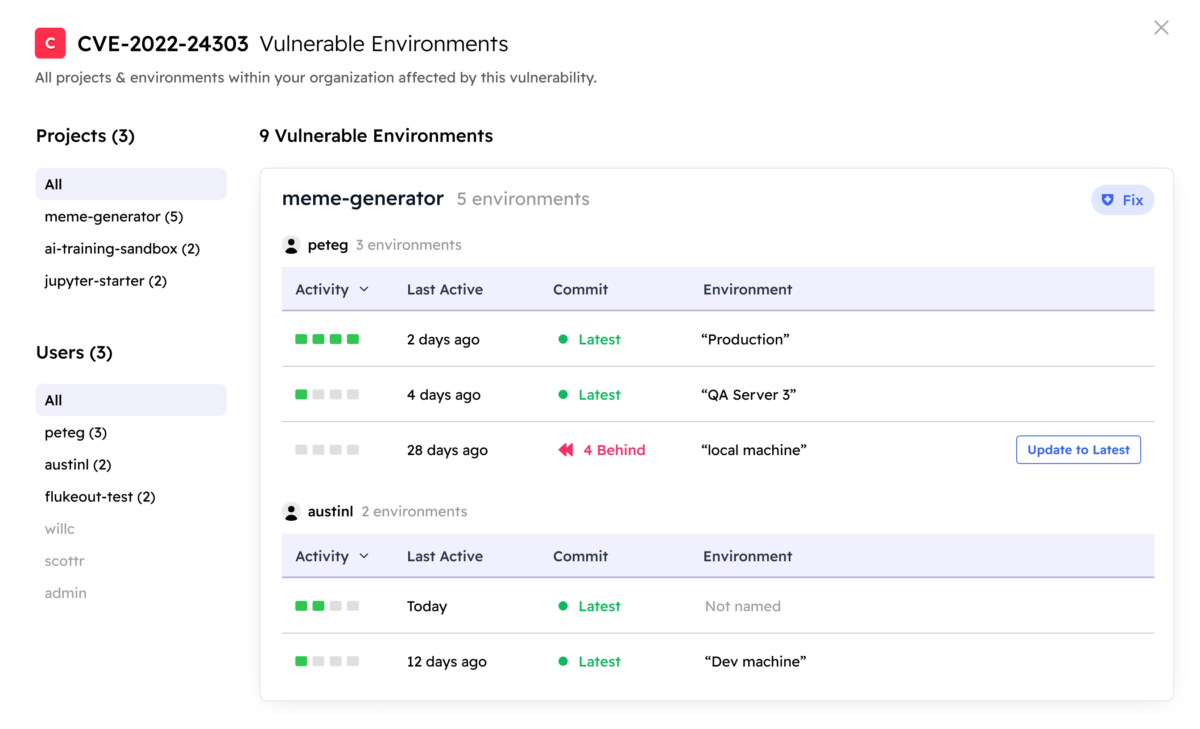
Are you CISA compliant?
Understand where you are in the process of conforming with the US Government ISV requirements.
Frequently Asked Questions
Why can’t I just use a tool like GitHub Actions or Azure DevOps for attestation?
Both GitHub and Azure have a plugin for their software build process that will indeed create an attestation for you. However, that attestation can only attest to the fact that the application was built securely using GitHub/Azure. It cannot attest to how the open source components within the application were built.
For example, most applications will include prebuilt open source software binaries within the code they submit to GitHub Actions/Azure DevOps. Those binaries were likely sourced from a public repository or built by the vendor themselves. In either case, since GitHub/Azure have no information about how these binaries were built/sourced, they cannot attest to whether they were created in a secure manner. This is what the ActiveState Platform provides.
How much of the Secure Software Development Framework (SSDF) do I need to implement?
To start, you need to comply with the CISA Attestations, which lets you “attest in good faith” that you’re progressing toward full SSDF adoption. This means you’ll only need to demonstrate competence in key areas initially. Remember, the deadline to submit your CISA attestation for critical software is June 8, 2024, and for in-scope software, it’s September 8, 2024. Time is of the essence: ISVs have resorted to hiring new resources and/or dedicating up to 30% of their developers time implementing SSDF requirements which are both broad and deep. This becomes a cost burden as well as detracts from time spent on innovation. However, by meeting these requirements and aligning with SSDF practices, you’ll not only ensure compliance but also significantly enhance your software’s security and your team’s capacity for innovation. Begin by reviewing your contract or agency requirements and adopt the SSDF practices that best meet those needs.
I work for an organization that is not very proactive when it comes to software supply chain security, what are the consequences?
- Severe Regulatory Penalties: Non-compliance can lead to hefty fines, starting at $20M.
- Increased Breach Risk: Since 2019, supply chain attacks have risen by 742%, exposing your sensitive government data if not handled.
- Large Financial Costs: Unidentified security holes can cost on average $4.45M USD per incident.
- Your leaders may get personally sued.
Why should I trust ActiveState to help me meet SSDF guidelines and CISA attestation requirements?
Great question! ActiveState has helped enterprises tame open source complexities for more than 20 years. We work with ISVs such as Boeing and Lockheed Martin across their Developer, Security, and Operations teams. Plus, ActiveState has the only solution available on the market today that can address the three key US government software supplier requirements in a single platform: a software attestation that can be used to prove your software is built securely, an SBOM in approved SPDX format, and a simple way to speed vulnerability remediation.
Where can I find out more information about all the government regulations impacting me?
- For context as to why the rules came about, start by reading The White House executive Order 14028 on Improving the Nation’s Cybersecurity.
- Next, learn more about the National Institute of Standards and Technology (NIST) and their Secure Software Development Framework (SSDF).
- Last but not least visit the Cybersecurity and Infrastructure Security Agency (CISA) website to read more about cybersecurity practices and regulations including the CISA attestation form that impact all federal contractors and vendors.
Connect with our security specialists for a demo.





