Tame the Complexity of Open Source







One platform. Total control.
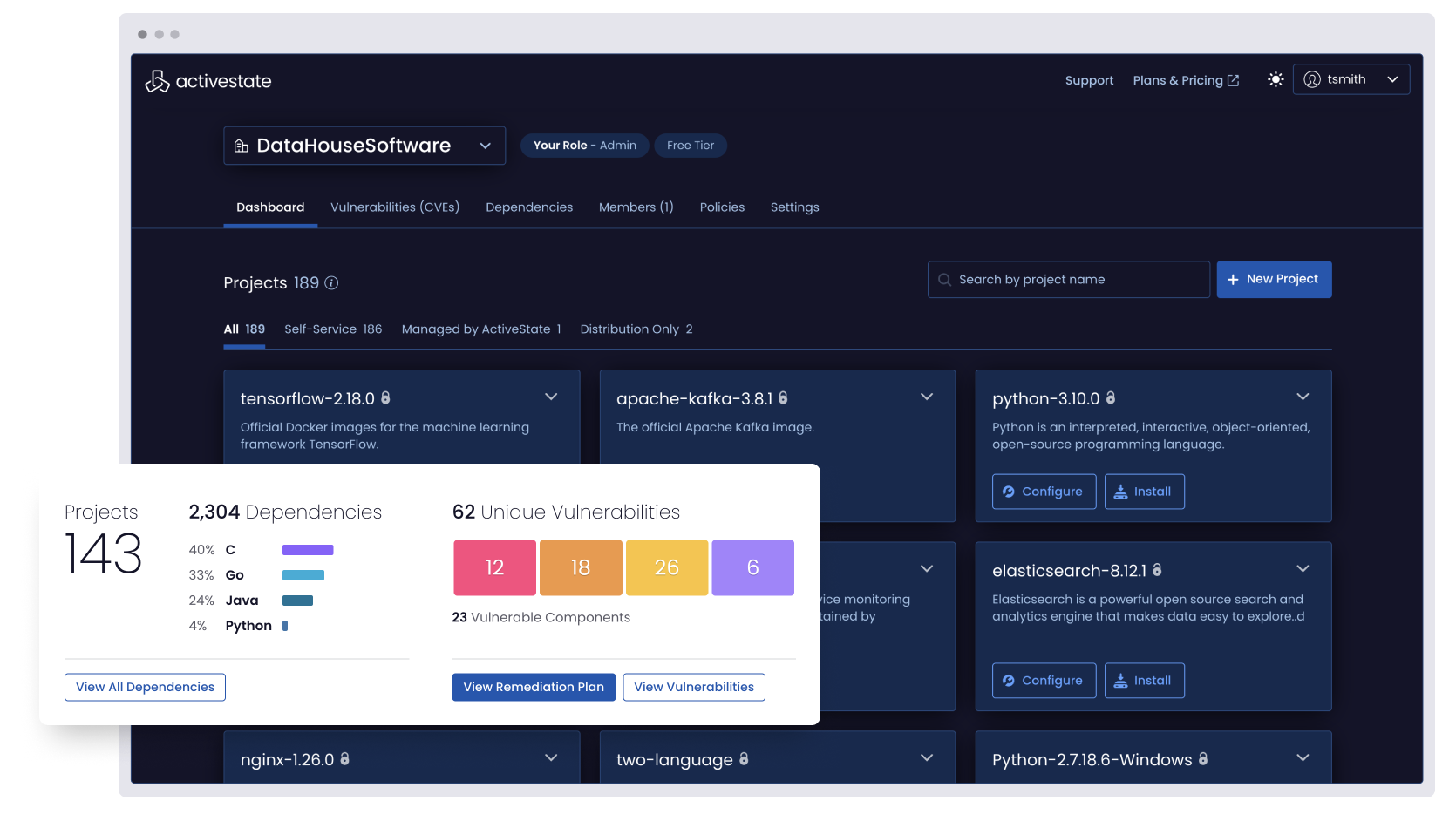
Discover: Unveil your open source landscape
Discover your complete open source landscape with comprehensive ingestion and real-time monitoring across SBOMs, repositories, and Kubernetes clusters.
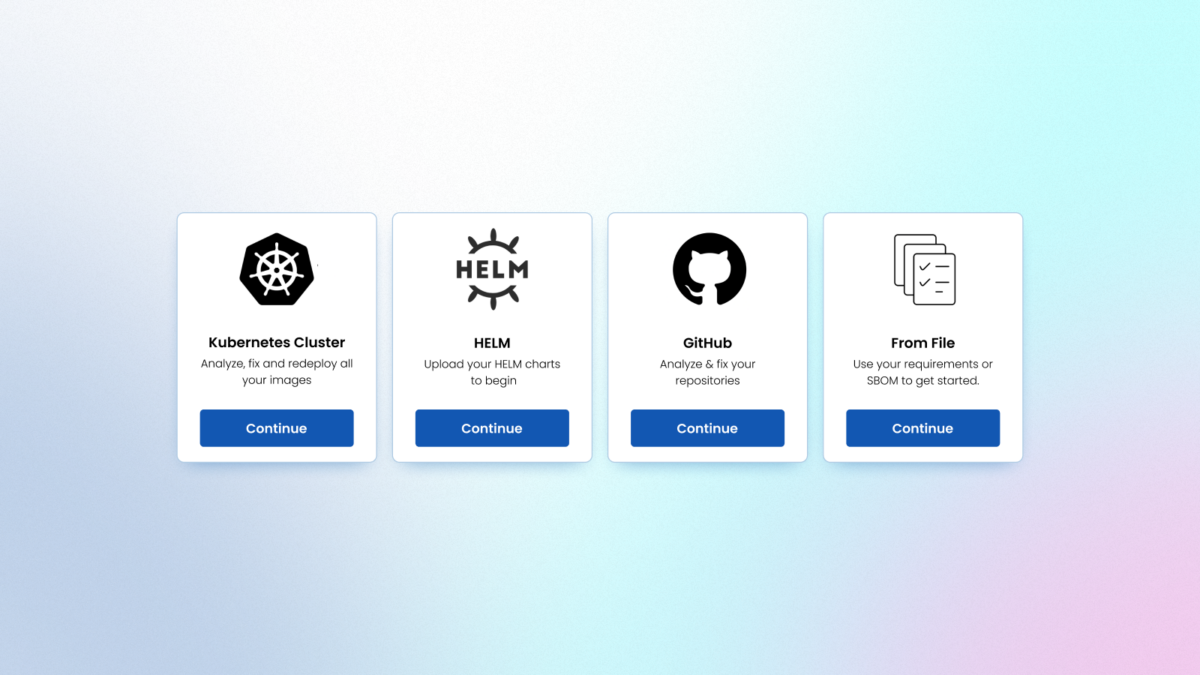
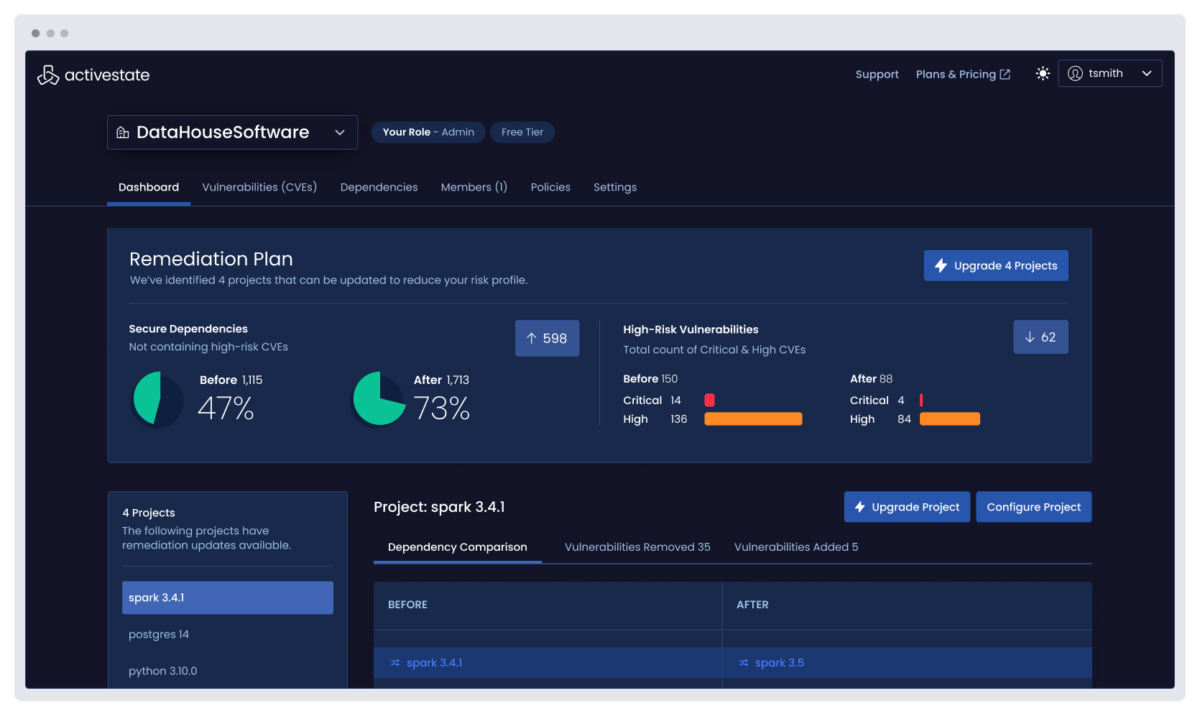
Prioritize: Uncover insights, mitigate risks
Prioritize actions through deep analytics, vulnerability assessments, and upgrade impact analysis that illuminate your risk profile.
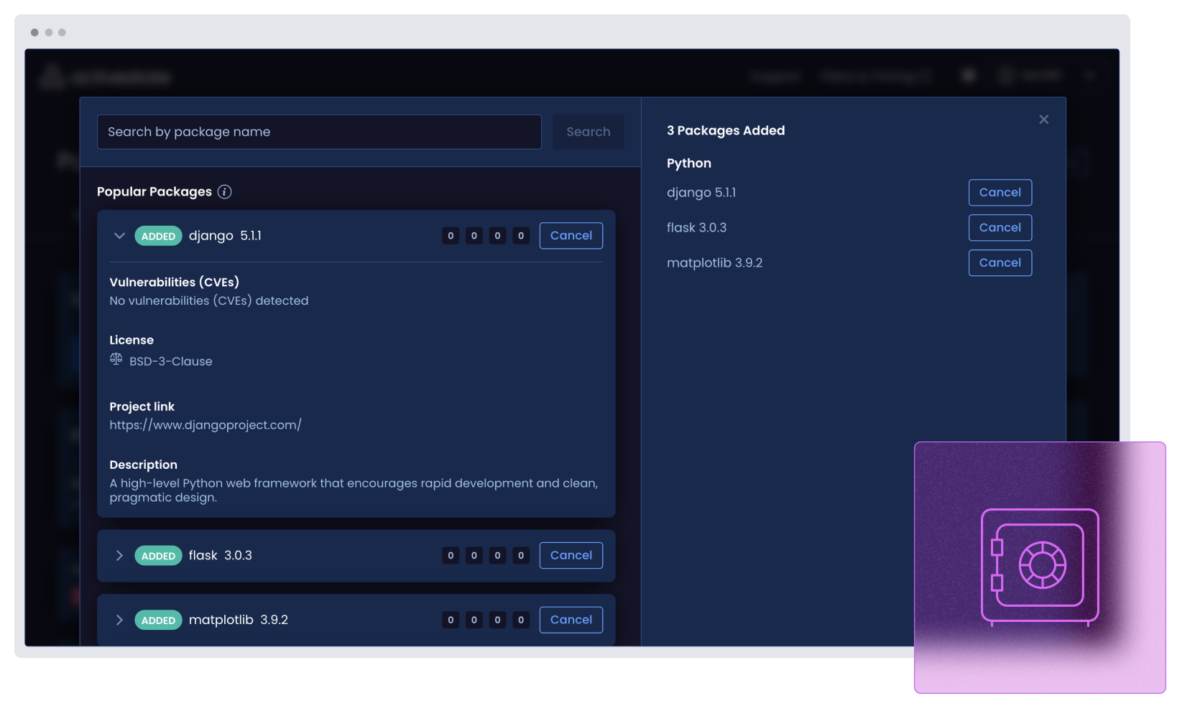
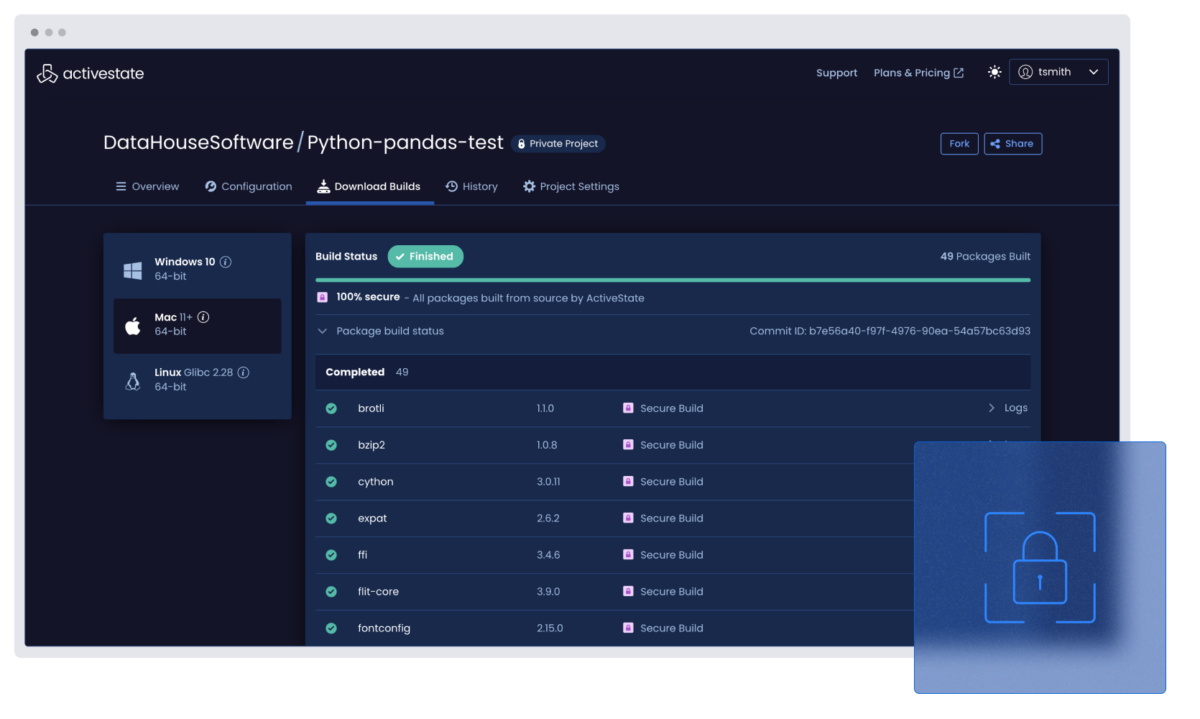
Curate and upgrade: Your secure open source gateway
Curate a secure gateway for trusted components with policy-driven filters and an immutable catalog built from verified source code.
Build and deploy: Your hardened build infrastructure
Build with confidence using our hardened infrastructure that integrates seamlessly into your CI/CD pipeline while maintaining security and compliance.




Additional Resources

ActiveState’s Groundbreaking Report Exposes Critical Gaps in Enterprise Vulnerability Remediation
The 2025 State of Vulnerability Management & Remediation Report Reveals that Reactive Approaches and Skills Shortages Plague Organizations [Vancouver, BC] – [March 6, 2025] Today,

Why VMaaS Is Important for Your Enterprise Cybersecurity Strategy
You’re exploring options for improving your cybersecurity strategy, and you’ve stumbled upon Vulnerability Management as a Service (VMaaS) as a potential solution. It promises to

The 2025 State of Vulnerability Management and Remediation Report
The ActiveState 2025 State of Vulnerability Management and Remediation Report provides a candid look into how organizations manage vulnerabilities and remediation.


